Hongsheng Technology’s first-phase business partner shareholding plan completed the stock purchase.
() Announcement was issued. As of the disclosure date of the announcement, the company has bought 26,113,67 shares of the company through secondary market purchase, with a turnover of 36,799,500 yuan (including transaction fees), accounting for 0.48% of the company’s total share capital. The first phase of the company’s business partner stock ownership plan has completed the stock purchase, and the above-mentioned purchased stocks will be locked in accordance with the regulations, and the lock-up period will be from August 31, 2021 to August 30, 2022.
The three shareholders of Guangxin Co., Ltd. intend to reduce their holdings by no more than 1.23%.
() It is announced that Mr. Zhao Qihua, the shareholder of the company, plans to reduce the company’s shares by no more than 3.89 million shares by block trading and centralized bidding, accounting for 0.84% of the company’s total share capital. Ms. Bai Dongmei, the shareholder of the company, plans to reduce the company’s shares by no more than 1.2 million shares through block trading and centralized bidding, accounting for 0.26% of the company’s total share capital. Mr. Wu Jianping, the shareholder of the company, plans to reduce the company’s shares by no more than 600,000 shares through block trading and centralized bidding, accounting for 0.13% of the company’s total share capital.
In the first half of the year, Haili Co., Ltd. accrued 30.823 million yuan for asset impairment.
() Announced that in order to truly reflect the company’s financial status and operating conditions in the first half of 2021, various assets of the company were comprehensively cleaned up and analyzed one by one in accordance with the Accounting Standards for Business Enterprises and the relevant provisions of the company’s accounting policies. Based on the principle of prudence, assets with signs of impairment were withdrawn accordingly, and the amount withdrawn in this period was 30.823 million yuan.
China’s new culture granted 6,487,900 restricted shares to 91 incentive targets for the first time.
() It was announced that the conditions for granting restricted shares for the first time stipulated in the Restricted Stock Incentive Plan (Phase I) (Draft) of Guoxin Culture Holdings Co., Ltd. have been achieved. According to the authorization of the second extraordinary general meeting of shareholders in 2021, the company held the third meeting of the tenth board of directors and the third meeting of the tenth board of supervisors on August 27, 2021, and reviewed and approved the Proposal on Granting Restricted Shares for the first time to the incentive objects. September 3, 2021 was determined as the first grant date, and 6,487,900 restricted shares were granted to 91 incentive targets at the grant price of RMB 6.942 per share.
Cits joint: The consortium won the bid for the tourism infrastructure construction project of Baihe Lake in guixi city.
() Announcement was issued. On August 30, 2021, the company received the Notice of Winning the Bid for the Construction of Housing Construction and Municipal Infrastructure Projects in Jiangxi Province, and the consortium where Guogui Wenlv was located officially became the winning bidder of Baihe Lake Project. The winning project: guixi city Baihe Lake Tourism Infrastructure Construction Project (EPC+O Mode), with a total winning cost of 132 million yuan.
Guiguang Network: China Sinochem began to handle the acquisition procedures of listed companies affiliated to Sinochem Group and China Chemical.
() On the evening of August 30th, it was announced that China Sinochem decided to go through the acquisition procedures of the listed companies owned by Sinochem Group and China Chemical in accordance with relevant regulations from August 30th. In March this year, with the approval of the State Council, Sinochem Group and China Chemical Industry jointly reorganized, and a new company was established, in which the State Council State-owned Assets Supervision and Administration Commission performed the investor’s duties on behalf of the State Council. Sinochem Group and China Chemical Industry were integrated into the new company.
AVIC Shen Fei nominated Song Shuiyun as a supervisor candidate.
() Make an announcement. The Board of Supervisors recently received a written resignation report from Mr. Nie Xiaoming. Mr. Nie Xiaoming applied to resign as chairman and supervisor of the board of supervisors of the company due to job changes.
On August 27th, 2021, the company held the 4th meeting of the 9th Board of Supervisors, deliberated and passed the Proposal on Nominating Candidates for Non-employee Representative Supervisors of the 9th Board of Supervisors of AVIC Shenfei, and agreed to nominate Mr. Song Shuiyun as the candidate for the 9th Board of Supervisors of the company, and submitted it to the second extraordinary shareholders’ meeting of the company in 2021 for election, with the term of office from the date of deliberation and approval by the shareholders’ meeting to the date of expiration of the term of the 9th Board of Supervisors of the company.
No.100 Holdings: It is planned to sell shares of Sanqi Mutual Entertainment.
() Announced on the evening of August 30th, the board of directors authorized the management to sell some or all of the shares held by () in due course when the investment income reached 10% or above. At present, the company holds 5,041,400 shares of Sanqi Mutual Entertainment, with a shareholding ratio of about 0.2%. The date of lifting the ban is expected to be September 10.
Zhong Zhichao, director of Yinlong Co., Ltd., has completed the cumulative reduction of 70,800 shares.
() Announcement was issued. On August 27th, 2021, Mr. Zhong Zhichao, the company’s director and senior manager, reduced his holding of 70,800 shares of the company through centralized bidding transaction, accounting for 0.008% of the company’s total share capital, and the reduction plan was completed.
No.100 Holdings intends to sell its shares in Sanqi Mutual Entertainment.
No.100 Holdings announced that in order to revitalize the existing assets, optimize the asset allocation and realize the investment income, the board of directors of the company authorized the management to sell part or all of the shares of Sanqi Mutual Entertainment in due course when the investment income reached 10% or above. The authorization matters include but are not limited to the transaction method, transaction timing, transaction price and signing of relevant documents. The authorization period is from the time when this matter is reviewed and approved by the board of directors until all the above financial assets are disposed of.
At present, the company holds 5,041,411 shares of Sanqi Mutual Entertainment, with a shareholding ratio of about 0.2%. The release date of the shares held is expected to be September 10, 2021 (subject to the approval of the exchange).
Red Dragonfly nominated Huang Xubin as a director candidate.
() Announced that Mr. Wang Jianbin, a non-independent director of the fifth board of directors of the company, applied to resign as a director of the company for personal reasons.
According to the Company Law and Articles of Association, the 12th meeting of the 5th Board of Directors of the Company reviewed and passed the Proposal on Resignation of the 5th Non-independent Directors and Nomination of Directors Candidates, and the Board of Directors nominated Mr. Huang Xubin as a director candidate of the Company.
Beijing Jishi, the shareholder of Dema Technology, has reduced its holdings by 5,690,400 shares.
Dema Technology announced that on August 30, 2021, the company received the Notice of Completion of the Share Reduction Plan of Zhejiang Dema Technology Co., Ltd. issued by Beijing Cornerstone Venture Capital Management Center (Limited Partnership)-Beijing Cornerstone Venture Capital Fund (Limited Partnership). By August 30, 2021, Beijing Cornerstone had reduced its shares by 5,690,400 shares through centralized bidding and block trading.
Jinjing Technology: Ignition Start of Photovoltaic Light Panel Production Line
() On the evening of August 30th, it was announced that the photovoltaic lightweight panel project of Ningxia Jinjing Technology Co., Ltd., a holding subsidiary of the company, was started on August 30th, and the equipment was connected with heat and adjusted. The product of this project is located in the solar photovoltaic panel, which is one of the important components of solar cells.
Fang Wen resigned as deputy general manager of Yunmei Energy.
() Announcement was issued. On August 30, 2021, the board of directors of the company received a written resignation report from Mr. Fang Wen, the company’s deputy general manager. Mr. Fang Wen applied to resign as the company’s deputy general manager due to work adjustment, and Mr. Fang Wen will no longer hold any position in the company after resigning.
Jiangxi-Guangdong Expressway: Changtai Company plans to invest in the expressway reconstruction and expansion project under its jurisdiction.
() Announcement: Jiangxi Changtai Expressway Co., Ltd. ("Changtai Company", with a shareholding ratio of 76.67%), the holding subsidiary of the company, is responsible for the reconstruction and expansion project of Zhangshu-Ji ‘an Expressway ("this reconstruction and expansion project"). The estimated total investment of this reconstruction and expansion project is 13.295 billion yuan, and the project funds are raised by domestic bank loans and Changtai Company.
According to the project plan, the planned route of this reconstruction and expansion project is basically consistent with the existing trend of this section of expressway, starting from the southern end of Zhangshu Hub of Nanchang-Zhangshu Expressway and ending at the northeast end of Ji ‘an South Hub of Jiangxi section of Daqing-Guangzhou Expressway. The main purpose is to expand the existing two-way four-lane into two-way eight-lane, with a total length of 104.861km, and it is planned to start in November 2021 with a construction period of four years.
It is reported that the implementation of this reconstruction and expansion project is in response to the "big cross" productivity layout put forward by the Second Plenary Session of the 13th Jiangxi Provincial Party Committee, and it is necessary to improve the traffic capacity and road service level of the north-south main shaft in the province. At the same time, this section of expressway is one of the company’s core road products. The implementation of this reconstruction and expansion can greatly improve its traffic capacity and service level, alleviate the traffic pressure of this section of expressway, improve the traffic experience of car owners and users, and have a positive effect on the company’s future business performance and long-term development, with remarkable social and economic benefits.
Tony Electronics’ application for non-public offering of shares was approved by China Securities Regulatory Commission.
() Announcement was issued. On August 30th, 2021, the issuance review committee of China Securities Regulatory Commission (hereinafter referred to as "China Securities Regulatory Commission") reviewed the company’s application for non-public offering of shares. According to the results of the meeting, the company’s application for non-public offering of shares was approved.
Tianrun Dairy’s application for non-public offering of shares was approved by CSRC.
() Announcement was issued. On August 30, 2021, the Issuance Review Committee of China Securities Regulatory Commission reviewed the company’s application for non-public offering of shares. According to the results of the meeting, the company’s application for non-public offering of shares was approved.
Li Jixi, the actual controller of Weipaige, reduced his holdings of 420,000 "Weipai Convertible Bonds"
() Announcement was issued. On August 30, 2021, the company received a notice from Mr. Li Jixi, the controlling shareholder and actual controller of the company. From August 16, 2021 to August 30, 2021, Mr. Li Jixi reduced his holdings of 420,000 Weipai convertible bonds through the trading system of Shanghai Stock Exchange, accounting for 10% of the total convertible bonds issued.
Wang Geng, Independent Director of Yibai Pharmaceutical, resigned.
() Announced that the board of directors of the company received a written resignation report from Ms. Wang Geng, an independent director of the company, on August 30, 2021. Ms. Wang Geng applied to resign as an independent director of the company for personal reasons. After resigning as an independent director of the company, Ms. Wang Geng no longer holds any position in the company.
No.100 Holdings recently received a total of 2,354,300 yuan from the government.
No.100 Holdings announced that on April 30, 2021, the company disclosed the government subsidies received from January 1, 2021 to the disclosure date of the announcement. From the last announcement to the date of disclosure, the company and its subsidiaries have received a total of 2,354,300 yuan of government subsidies.
According to the relevant provisions of the Accounting Standards for Business Enterprises No.16-Government Subsidies, the above-mentioned government subsidies related to assets and income totaled 2,354,300 yuan, of which the government subsidies related to assets were recognized as deferred revenue, which were included in the profits and losses by stages within the service life of related assets; Government subsidies related to income are listed as other income and included in current profits and losses.
Xing Boyue, a shareholder of Jinhua, has increased his shareholding by 1%.
() Announcement was issued. On August 30th, the company received a notice from Xing Boyue, a shareholder. From August 14th to August 30th, 2021, Xing Boyue increased his holding of 3,731,400 shares of the company through the secondary market call auction method, accounting for 1% of the company’s total share capital. After this increase, Xing Boyue and his concerted actions hold a total of 87.1573 million shares of the company, accounting for 23.35% of the company’s shares, and have become the largest shareholder.
Xinke Materials was reduced by a total of 39,689,400 shares by four shareholders. The reduction plan was completed.
() Announcement. Recently, the company received letters from natural person shareholders Dongjiang Weixiong, Hu Chunhui, Jiang Qiuyi and Chen Guo about the results of reducing the company’s shares. The above shareholders reduced their holdings by a total of 39,689,400 shares, and the implementation of this reduction plan was completed.
Most of the products have completed the issuance of 2 billion yuan medium-term notes.
() Announcement: On August 26th, 2021, the company issued the second phase of medium-term notes in 2021. The actual total amount of medium-term notes issued in this period was 2 billion yuan, and the issue interest rate was 4.2%.
Sanqi Mutual Entertainment intends to apply for a total bank credit line of no more than 6 billion yuan.
Sanqi Entertainment announced that the bank credit line applied by the company in 2020 will expire soon. In order to ensure the continuity of the company’s bank credit line and to better support the business development needs of the company and its subsidiaries, the board of directors agreed that the company and its subsidiaries should apply to financial institutions such as China Merchants Bank Co., Ltd., Shanghai Pudong Development Bank Co., Ltd. and Bank of Communications Co., Ltd. for a comprehensive credit line with a total amount not exceeding RMB 6 billion or other equivalent currencies.
This application for bank credit line still needs to be submitted to the shareholders’ meeting of the company for deliberation, and the authorization resolution is valid for one year, counting from the date of deliberation and approval by the shareholders’ meeting. Within the above credit line, the credit can be used repeatedly.
Sanqi Mutual Entertainment intends to apply for a total bank credit line of no more than 6 billion yuan.
Sanqi Entertainment announced that the bank credit line applied by the company in 2020 will expire soon. In order to ensure the continuity of the company’s bank credit line and to better support the business development needs of the company and its subsidiaries, the board of directors agreed that the company and its subsidiaries should apply to financial institutions such as China Merchants Bank Co., Ltd., Shanghai Pudong Development Bank Co., Ltd. and Bank of Communications Co., Ltd. for a comprehensive credit line with a total amount not exceeding RMB 6 billion or other equivalent currencies.
This application for bank credit line still needs to be submitted to the shareholders’ meeting of the company for deliberation, and the authorization resolution is valid for one year, counting from the date of deliberation and approval by the shareholders’ meeting. Within the above credit line, the credit can be used repeatedly.
Nanjing-Shanghai Expressway completed the issuance of 900 million yuan ultra-short-term financing bonds.
() Announcement was issued. On August 25th and 26th, 2021, the company issued the 24th and 23rd ultra-short-term financing bonds in 2021 respectively. Among them, in 2021, the twenty-third ultra-short-term financing bonds were actually issued with a total amount of 400 million yuan and a term of 176 days. In 2021, the 24 th ultra-short-term financing bonds were actually issued with a total amount of 500 million yuan and a term of 176 days.
Petrochina project: the net profit in the first half of the year increased by 74.21% year-on-year, and the newly signed contract value was 46.362 billion yuan.
() On the evening of August 30th, it was announced that in the first half of 2021, the construction of key projects was promoted efficiently, the market development took on a new look, and the market structure was continuously optimized. Realized operating income of 32.704 billion yuan, a year-on-year increase of 15.37%; The net profit of returning to the mother was 481 million yuan, a year-on-year increase of 74.21%. In the first half of the year, the company signed 46.362 billion yuan of new contracts, 7.891 billion yuan of contracts that have been won but not signed, and 10.342 billion yuan of contracts that have been signed but not yet come into effect.
Caitong Securities completed the issuance of 2.5 billion yuan short-term financing bonds.
() Announcement: The sixth short-term financing bonds of the company in 2021 were issued on August 27th, 2021, with the actual total issuance of RMB 2.5 billion, accounting for 2.39% in coupon rate.
Huarong Holdings: It plans to terminate the purchase of 80% equity of Shenrui Bio by issuing shares and paying cash.
The financial network announced on August 30th that it intends to terminate the purchase of 80% equity of Wuxi Shenrui Biological Products Co., Ltd. held by Sheng Qingsong and others by issuing shares and paying cash, and raise matching funds.
Beijing Investment Development provides Sun Company with a loan guarantee of no more than 1 billion yuan.
On August 30th, () Co., Ltd. issued an announcement on providing guarantee for the loan of Beijing Jingtou Xingtan Real Estate Co., Ltd., with the total amount of guarantee not exceeding RMB 1 billion.
According to the new media of Viewpoint Real Estate, in order to raise funds for project development and construction, Jingtou Xingtan intends to apply for a development loan from a financial institution, the amount of which is no more than RMB 1 billion, and the company or its holding subsidiary will provide joint liability guarantee with a maximum amount of no more than RMB 1 billion for this business. Jingtou Xingtan is a wholly-owned sun company, so there is no counter-guarantee in this guarantee.
By June 30, 2021, the total assets of Jingtou Xingtan were 3,812,846,400 yuan and the total liabilities were 3,829 million yuan, including 260 million yuan of bank loans, 2,903 million yuan of current liabilities and-15,790,600 yuan of net assets. From January to June 2021, the operating income was zero and the net profit was-2,416,000 yuan (the data was unaudited).
It is also known that as of July 31, 2021, the balance of external guarantees of the company and its wholly-owned subsidiaries was 21.06 billion yuan, accounting for 329.56% of the company’s audited net assets in 2020.
Beijing Investment Development Co., Ltd. plans to participate in the cornerstone of Xinchuang’s layout of information technology application and innovation related industries
According to the announcement of Beijing Investment Development, the company intends to participate in the investment of Beijing Cornerstone Xinchuang Venture Capital Center (Limited Partnership) (tentatively named "Cornerstone Xinchuang") as a limited partner. The total subscribed capital contribution of Cornerstone Xinchuang this time is RMB 300.05 million, and the company plans to subscribe capital contribution of RMB 100 million in cash, accounting for 33.33%.
IT is reported that Cornerstone Xinchuang will fully learn from the operation mode of international mature market industrial funds, combine with the direction of China’s economic development, focus on the application and innovation of information technology related industries, and focus on the growth enterprises in target industries such as information security, industrial Internet, artificial intelligence, IT infrastructure and related applications for equity investment, and mainly select enterprises with high growth in related industries, outstanding core competitiveness and potential to grow into leading sub-sectors in the future for equity investment.
() tianjin binhai hi-tech industrial development area Management Committee plans to collect and store land in B7-B9 plot of BPO base.
Haitai Development announced that Tianjin Binhai New Area Land Development Center and tianjin binhai hi-tech industrial development area Planning and Natural Resources Bureau signed the Tripartite Agreement on Land Acquisition with the company, and the B7-B9 plot of the company’s BPO base was collected and stored, covering an area of 89,140.3 square meters (133.7 mu), and the comprehensive land compensation fee was 85.129 million yuan.
According to the announcement, this land purchasing and storage is a transaction that the company supports the comprehensive development and utilization of land resources in Tianjin Binhai High-tech Industrial Development Zone and responds to the land planning requirements of Tianjin Binhai High-tech Industrial Development Zone. The funds received by the company through this purchasing and storage will be used to supplement the company’s working capital.
Zhaoyi Innovation: The two shareholders intend to reduce their shares by 3.21%.
() On the evening of August 30th, it was announced that Zhu Yiming, a shareholder, and topview, Hong Kong, were allowed to reduce their shares through centralized bidding and/or block trading, and Zhu Yiming planned to reduce the company’s shares by no more than 13.28 million shares and no more than 2% of the company’s total share capital; Topview Co., Ltd. plans to reduce its shareholding by no more than 8.06 million shares and no more than 1.21% of the total share capital of the company.
Core original shares: Director Zhang Shuai resigned.
Core original shares announcement, the company’s board of directors recently received a written resignation report submitted by company director Zhang Shuai. Zhang Shuai applied to resign as a director of the first board of directors and a member of the strategy committee of the first board of directors due to work adjustment, and will not hold any post in the company after his resignation. His resignation report will take effect as of the date when it is delivered to the board of directors.
In addition, on August 30, 2021, the board of directors of the company reviewed and approved the Proposal on Nominating Candidates for Directors and the Proposal on Adjusting the Members of the Strategy Committee of the First Board of Directors, and agreed to nominate Sun Guodong as a candidate for the first board of directors, and agreed that Sun Guodong would serve as a member of the Strategy Committee of the first board of directors after he officially became a director of the company, and his term of office would be from the date when the third extraordinary shareholders’ meeting of the company was reviewed and approved in 2021 to the date when the term of office of directors of the first board of directors of the company expired.
Xinhua medical: Abdominal endoscopic high-frequency surgical instruments obtained the registration certificate of three kinds of medical instruments.
() Announcement, Xinhua Surgical Instrument Co., Ltd., a holding subsidiary of the company, recently received the People’s Republic of China (PRC) Medical Device Registration Certificate issued by National Medical Products Administration. Product name: high-frequency surgical instrument for abdominal endoscope.
It is reported that the high-frequency surgical instrument of abdominal endoscope is used in conjunction with the high-frequency generator. Among them, the unipolar grasping forceps and the unipolar separating forceps adopt a three-disassembly and quick-disassembly split structure, which realizes arbitrary assembly and solves complicated operations such as alignment and lifting during disassembly and assembly. Blind disassembly and blind assembly can accurately align, which is convenient and fast. For patients, the operation carried out with such products has many advantages, such as quick recovery, short hospitalization time, good abdominal beauty effect, and reducing the burden on patients.
Huang Ping, director of Shenghe Resources, reduced his holdings of 7.963 million shares for more than half of the time.
() Announcement was issued. By August 27th, 2021, Mr. Ping Huang, the director, and Mr. Wang Xiaohui, the director, had reduced their holdings for more than half of this reduction plan. During this period, Mr. Ping Huang reduced his holdings of 7.363 million shares of the company through centralized bidding, accounting for 0.42% of the company’s total share capital; Mr. Wang Xiaohui reduced his holding of 600,000 shares of the company through centralized bidding transaction, accounting for 0.03% of the company’s total share capital. This reduction plan has not yet been implemented.
There is no information that should be disclosed but not disclosed in the stock price change of Hebang Bio.
() It is announced that the daily closing price of the company’s stock price has deviated by more than 20% for three consecutive trading days on August 26th, 27th and 30th, 2021, which is an abnormal fluctuation of stock trading according to the relevant provisions of the Trading Rules of Shanghai Stock Exchange.
After the company’s self-examination and sent a letter to the controlling shareholder and actual controller for verification, as of the disclosure date of this announcement, there are no major matters that should be disclosed but not disclosed.
Achievement of Exercise Conditions in the First Exercise Period of Bozhong Seiko’s 2020 Stock Option Incentive Plan
Bozhong Seiko issued an announcement, held the sixth meeting of the second board of directors and the sixth meeting of the second board of supervisors on August 30, 2021, and reviewed and approved the Proposal on the Achievement of Exercise Conditions in the First Exercise Period of the Company’s 2020 Stock Option Incentive Plan. The exercise conditions of the first exercise period of the company’s 2020 stock option incentive plan have been achieved.
According to the relevant provisions of the Option Incentive Plan, the board of directors agreed to cancel 1,531,500 stock options corresponding to the first exercise period of this incentive plan in view of the fact that the company’s net profit in 2020 was lower than that in 2019 and the company-level performance appraisal in the first exercise period of this incentive plan was not fully up to standard. In view of the fact that 32 incentive objects are no longer qualified as incentive objects due to resignation, the Board of Directors agreed to cancel 800,000 stock options that have been granted to these 32 people but have not yet exercised.
Andy Su: China Sinochem will indirectly acquire 85.95% of the shares of the company.
() Announcement: On August 30, 2021, the company received the Explanation of China Sinochem Holdings Co., Ltd. on Starting Relevant Procedures of Joint Reorganization issued by China Sinochem Holdings Co., Ltd. ("China Sinochem"), and China Sinochem decided to handle the acquisition procedures of listed companies affiliated to Sinochem Group and China National Chemical Corporation in accordance with relevant regulations from the date of issuance of the explanation.
It is reported that the State-owned Assets Supervision and Administration Commission of the State Council ("the State Council State-owned Assets Supervision and Administration Commission") transferred all the shares of China Sinochem Group Co., Ltd. ("Sinochem Group") to China Sinochem without compensation, which led to China Sinochem’s indirect acquisition of 85.95% of the shares held by the holding companies under China National Chemical Group.
After the acquisition, China Sinochem indirectly controlled 2.301 billion shares (accounting for 85.81% of the company’s total share capital) through Bluestar Group, a subsidiary of China National Chemical Corporation, and indirectly controlled 3.7373 million shares (accounting for 0.14% of the company’s total share capital) through Beijing Rubber Industry Research and Design Institute Co., Ltd., a wholly-owned subsidiary. The controlling shareholder of the company is still Blue Star Group, and the actual controller is still the State Council State-owned Assets Supervision and Administration Commission.
The amount of factoring financing business applied by Huafa Co., Ltd. to related parties shall not exceed 600 million yuan.
() It is announced that Zhuhai Huaguo Trading Co., Ltd. ("Huaguo Trading"), a wholly-owned subsidiary of the company, intends to transfer its accounts receivable to Huajin International Commercial Factoring (Zhuhai) Co., Ltd. ("Huajin Factoring"), and Huajin Factoring will carry out accounts receivable factoring financing business for it. The amount of this factoring financing shall not exceed RMB 600 million (including the principal amount, the same below).
According to the announcement, Zhuhai Huafa Investment Holding Group Co., Ltd. ("Huafa Investment Holding Group") holds 100% equity of Zhuhai Huachuang Investment Management Co., Ltd. ("Huachuang Investment"), and Huachuang Investment holds 100% equity of Huajin Factoring; Huafa Investment Control Group and the Company belong to related parties under the same control of Zhuhai Huafa Group Co., Ltd. ("Huafa Group"), and this transaction constitutes a related party transaction.
Yang Jianmin, a shareholder of Deawell, has reduced his shareholding by 1%.
Deawell announced that on August 30th, the company received a notice from Yang Jianmin, a shareholder, that the shareholding ratio of shareholders had reached 1%. After this equity change, Yang Jianmin’s shareholding in the company decreased from 11.17% to 10.17%; Yang Jianmin and Ms. Yang Shu, who acted in concert, reduced the total share of the company from 14.35% to 13.35%.
Zhu Yiming, the shareholder of Zhaoyi Innovation, and others intend to reduce their holdings by no more than 21.34 million shares.
Zhaoyi Innovation announced that Mr. Zhu Yiming, the shareholder of the company, and Hong Kong topview De Co., Ltd. intend to reduce their shares through centralized bidding and/or block trading. The reduction period is: within 6 months after 15 trading days from the disclosure date of this announcement, and within 6 months after 5 trading days from the disclosure date of this announcement. Mr. Zhu Yiming intends to reduce the company’s shares by no more than 13.28 million shares and no more than about 2% of the company’s total share capital; Topview Co., Ltd. plans to reduce its shareholding by no more than 8.06 million shares and no more than 1.21% of the total share capital of the company.
Starting conditions for triggering measures to stabilize stock prices (1) Controlling shareholders, directors and senior executives intend to increase their holdings of company shares by 1.007 million yuan to 3.0189 million yuan.
On the evening of August 30th, Garden Co., Ltd. announced that the controlling shareholder, directors and senior managers of the company planned to increase their holdings of the company’s shares by a total of RMB 1.007 million to RMB 3.0189 million in order to stabilize the company’s share price.
Specifically, Hangzhou Yuanrong Investment Group Co., Ltd., the controlling shareholder of Garden Co., Ltd., has accumulated an amount of not less than 784,100 yuan and not more than 2.352 million yuan. It is estimated that the shareholding ratio will not exceed 2% of the company’s total share capital. The accumulated amount used by the company’s directors (except independent directors) and senior management personnel to increase the company’s shares is not less than 222,900 yuan and not more than 666,900 yuan.
It is understood that from July 28 to August 24, the closing price of Garden shares has been lower than the ex-dividend issue price of 16.28 yuan per share for 20 consecutive trading days, which triggered the starting conditions for measures to stabilize stock prices. As of the close of August 30, Garden shares reported 15.36 yuan/share, still lower than the ex-dividend issue price.
Ni Shoucai, director of Aofu Environmental Protection, and others intend to reduce their holdings by no more than 280,000 shares.
Aofu Environmental Protection announced that due to the need of personal funds, from September 23, 2021 to March 20, 2022 after 15 trading days from the disclosure date of this announcement (during the window period, when shares cannot be reduced, etc.), Mr. Ni Shoucai, the director and senior manager of the company, intends to reduce his holdings of the company’s shares by means of centralized bidding transaction, and the amount of reduction will not exceed 240,000 shares, accounting for 0.31% of the company’s total share capital; Mr. Zhang Xuguang, the supervisor, intends to reduce his shares in the company by centralized bidding, and the number of shares to be reduced shall not exceed 40,000 shares, accounting for 0.05% of the total share capital of the company.
Liu Hongyue, deputy general manager of Aofu Environmental Protection, has reduced his holding of 379,600 shares.
Aofu Environmental Protection announced that as of August 27th, Mr. Liu Hongyue, the director, deputy general manager and core technician, reduced his holdings by 379,600 shares through centralized bidding, accounting for 0.49% of the total shares of the company, and the period of this reduction plan expired.
In the first half of Blu-ray development, the net profit loss of returning to the mother was 4.721 billion, and the financial expenses more than doubled.
On August 30th, Sichuan () Co., Ltd. announced that from January to June, 2021, the company achieved operating income of 11.931 billion yuan, a year-on-year decrease of 24.51%. Realized a total profit of-5.079 billion yuan; The net profit loss attributable to shareholders of listed companies was 4.721 billion yuan.
During the reporting period, Blu-ray’s real estate development business achieved a sales amount of 34.39 billion yuan and a sales area of 3.3582 million square meters, of which the sales amount of consolidated statements was 22.955 billion yuan; The newly started area of the project is 2,751,600 square meters, and the completed area is 2,219,900 square meters.
The announcement pointed out that the decrease in operating income was mainly due to the decrease in the number of properties that met the carry-over conditions during the reporting period compared with the same period of last year, but the operating costs in the same period increased, reaching 12.556 billion yuan, up 9.24% year-on-year.
It is worth noting that among the three expenses, the financial expenses of Blu-ray development in the first half of 2021 also increased substantially, with a year-on-year increase of 226.87%, reaching 1.077 billion yuan. Blu-ray development is explained by the fact that some of the new loans with tight liquidity were not directly used for project construction, and the expensed amount of loan fees increased compared with the same period of last year.
According to Viewpoint Real Estate New Media, as for debt, as of June 30, 2021, the total assets of Blu-ray Development were 220.593 billion yuan, with the asset-liability ratio of 84.01% and the net debt ratio of 227.78% after deducting advance receipts.
Blu-ray Development said that at present, with the joint efforts of financial supervision departments, local government departments and companies, the overall plan for debt risk resolution is being stepped up. At the same time, the company is also fully coordinating all parties to actively raise funds, striving to restore the normal operation of the company, and taking various measures to carry out self-help.
These include: ensuring the stability of the workforce and the integrity of core assets to the greatest extent, and creating good endogenous conditions for the success of the overall risk resolution work; Ensure development and stable delivery, actively communicate with regional governments for the existing projects, take multiple measures simultaneously, manage them in different categories, and do our best to ensure the normal operation of the projects; Expand our thinking, pay attention to residential sales, all kinds of payments, revitalize assets, focus on strengthening the management of payment structure and value structure, and build a full-cycle pricing control mechanism to ensure positive business cash flow; Hold down expenses, reduce costs, comprehensively reduce sales management expenses, improve organizational efficiency and strengthen cost control by streamlining headquarters, improving efficiency and reducing management levels.
It is understood that as of June 30, 2021, the balance of monetary funds for Blu-ray Development was 10.029 billion, including 330 million freely available funds and 9.699 billion yuan with various restricted or restricted uses. The above-mentioned 9.699 billion yuan specifically includes 6.405 billion yuan of project pre-sale supervision funds, 2.443 billion yuan of co-management funds with partners, 109 million yuan of overseas restricted funds, and 742 million yuan of various deposits and funds frozen due to lawsuits. All the above-mentioned restricted or limited-use funds cannot be freely used by the company or returned to the debts of financial institutions.
Kweichow Moutai: Recommend Ding Xiongjun as the chairman of the company, and Gao Weidong leaves office.
On the afternoon of August 30th, () announced that according to the relevant documents of Guizhou Provincial People’s Government, Ding Xiongjun was recommended as the candidate for the director and chairman of Guizhou Maotai Liquor Co., Ltd. (hereinafter referred to as the company), and it was suggested that Gao Weidong no longer serve as the chairman and director of the company. The Company will convene a board meeting and a general meeting of shareholders as soon as possible in accordance with laws, regulations and the Articles of Association to review the above-mentioned job adjustment, which will take effect after being reviewed and approved by the board meeting and the general meeting of shareholders.
According to the announcement, Ding Xiongjun, male, Han nationality, born in Chongyang, Hubei Province, was born in August 1974, joined the work in July 1995, and joined the Communist Party of China (CPC) in June 1994 with a postgraduate degree and a doctor of science. He is currently a member, secretary, director and chairman of the Party Committee of Kweichow Moutai Distillery (Group) Co., Ltd. in China.

(Editor: Xin Li)
Lianshun Technology, the major shareholder of Qinghai Huading, plans to reduce its holdings by no more than 4.38 million shares.
() Announced that Lianshun Technology, the largest shareholder of the company, intends to reduce its shareholding by no more than 4.38 million shares (accounting for 0.998% of the company’s total share capital) within 3 months after 15 trading days from the date of this announcement.
Wang Geng, Independent Director of Yibai Pharmaceutical Company, resigned.
On August 30th, Yibai Pharmaceutical announced that the board of directors had received a written resignation report from Wang Geng, an independent director of the company. For personal reasons, Wang Geng applied to resign as an independent director of the company. After Wang Geng resigned as an independent director of the company, he no longer held any position in the company.
In view of the fact that Wang Geng’s resignation will cause the number of independent directors in the company to be less than one third of the board members and the number of independent directors in the nomination committee, audit committee and remuneration and assessment committee of the company’s board of directors to be less than the quorum, according to the Company Law, the Articles of Association, the Guidelines for Independent Directors of Listed Companies (revised in 2020) and other relevant regulations, Wang Geng’s resignation application will produce new independent directors in the company by-election according to relevant regulations, and ensure that the board of directors and the nomination committee, audit committee and assessment committee of the board of directors of the company. Prior to this, in order to ensure the normal operation of the board of directors, Wang Geng will continue to perform his duties as an independent director in accordance with relevant laws and regulations. The company will complete the election of new independent directors and relevant special committees of the board of directors as soon as possible in accordance with relevant legal procedures and fulfill its information disclosure obligations in a timely manner.
Maotai changed coaches! Recommend Ding Xiongjun as the chairman candidate. Gao Weidong has been in office for less than a year and a half.
Hongxing capital bureau original
Reporter | Yu Yao Deng Lingyao
Editor | Ren Zhijiang Internship Editor | Yu Dongmei
On August 30th, Kweichow Moutai announced that according to the relevant documents of Guizhou Provincial People’s Government, Ding Xiongjun was recommended as the candidate for the director and chairman of Kweichow Moutai Co., Ltd., and it was suggested that Gao Weidong no longer serve as the chairman and director of the company.
Official website, the Guizhou Provincial People’s Government, stated in the Notice on the Post Adjustment of Comrade Ding Xiongjun that the post adjustment of the above personnel should be handled in accordance with the Company Law of People’s Republic of China (PRC) and relevant regulations.
Previously, on March 3, 2020, Kweichow Moutai announced that, according to the relevant documents of Guizhou Provincial People’s Government, Comrade Gao Weidong was recommended as the candidate for the director and chairman of Kweichow Moutai Co., Ltd., and Comrade Li Baofang was suggested not to serve as the chairman and director of the company. In other words, Gao Weidong has been in office for less than a year and a half.

(): Notice of Approval of SHR-1701 Injection and SHR-A1912 for Injection for Drug Clinical Trial.
Hengrui Pharma issued an announcement. Recently, Suzhou Shengdiya Biomedical Co., Ltd. and Shanghai Hengrui Pharma Co., Ltd., the subsidiaries of the company, respectively received the Notice of Approval for Drug Clinical Trial on SHR-1701 Injection and SHR-A1912 for Injection from National Medical Products Administration (hereinafter referred to as "National Medical Products Administration"), and will conduct clinical trials in the near future.
It is reported that SHR-1701 can promote the activation of effector T cells, at the same time, it can effectively improve the immunomodulation in tumor microenvironment, and finally effectively promote the immune system to kill tumor cells. SHR-A1912 for injection is an antibody drug conjugate (ADC) targeting tumor-specific antigen. By binding with the target antigen on the tumor surface, the drug is swallowed into tumor cells and then released small molecular toxins to kill tumor cells.
* Dexin Investment, the controlling shareholder of ST Dexin, intends to reduce its holdings by no more than 9.6 million shares.
() Announced that due to the capital demand of the controlling shareholder Delixi Xinjiang Investment Group Co., Ltd. (hereinafter referred to as "Dexin Investment"), it is planned to reduce its shareholding by no more than 9.6 million shares (accounting for 6% of the company’s total share capital) within 6 months after 15 trading days from the date of this announcement.
Aili Home intends to set up an overseas joint venture with its main customer HMTX to build a production base.
() Announcement, the company plans to jointly invest with HMTX Industries, LLC ("HMTX") to set up an overseas holding subsidiary, American Flooring LLC (Chinese name: American Flooring Co., Ltd., "American Company" or "Joint Venture Company") in the United States, so as to build a "luxury vinyl flooring production base" in the United States and be responsible for the research, development, production and sales of luxury vinyl flooring in the United States. The total planned investment of the joint venture company is USD 30 million, of which the equity ratio of the company is 51% and that of HMTX is 49%.
It is reported that this foreign investment is an important step for the company to implement the strategy of capacity globalization and build a dual-cycle development pattern. The establishment of the joint venture company can significantly enhance the company’s ability to supply and serve the North American market nearby, greatly reduce the impact of political risks and poor logistics on business continuity, and effectively enhance the toughness and efficiency of the entire supply chain. Through the form of equity cooperation, deep binding and strong alliance with major customers will further enhance the company’s position in the supply chain and the middle and high-end elastic flooring market in North America. In the long run, it will also promote the company’s own international operation capacity building and lay the foundation for the company’s future global layout.
Taiping Bird received a government subsidy of 66.6191 million yuan.
() It was announced that Ningbo Taiping Bird Fashion Clothing Co., Ltd. and some of its subsidiaries and Sun Company received a total of 66.6191 million yuan of government subsidies from June 1, 2021 to August 30, 2021, all of which were related to income.
Expand business field Tianyong Intelligent plans to invest 200 million yuan to set up a wholly-owned subsidiary.
() Announced that due to the needs of business development, the company plans to invest and set up a wholly-owned subsidiary "Jiangsu Tianyong Intelligent Engineering Co., Ltd." (referred to as "Jiangsu Tianyong") through its own funds and direct or indirect financing, with an investment amount of RMB 200 million.
The purpose of establishing Jiangsu Tianyong Intelligent Engineering Co., Ltd. this time is to further upgrade products, expand the company’s business field and implement the company’s strategic planning, which is conducive to improving the company’s overall operation level and laying a good foundation for the company’s future development.
From January to June, ST Xiyuan made provision for impairment of receivables of about 13,715,900 yuan.
() Announcement was issued. According to the Accounting Standards for Business Enterprises and the relevant provisions of the company’s accounting policies and accounting estimates, in order to truly and fairly reflect the company’s financial position on June 30, 2021 and its operating results from January to June 2021, based on the principle of prudence, the company and its subsidiaries made provision for impairment of receivables of about 13,715,900 yuan.
Zhongtian Submarine Cable, a subsidiary of Zhongtian Technology, received the decision of Shanghai Stock Exchange to terminate the audit.
() Announcement: On August 27, 2021, Zhongtian Submarine Cable, a subsidiary of the company, submitted an application to the Shanghai Stock Exchange to withdraw the application documents for initial public offering and listing in science and technology innovation board, and on August 30, 2021, it received the "Decision on Terminating the Examination of Initial Public Offering and Listing in science and technology innovation board" from the Shanghai Stock Exchange. The Shanghai Stock Exchange decided to terminate the examination of the initial public offering of Zhongtian Technology Submarine Cable Co., Ltd. and its listing in science and technology innovation board.
Pan Liansheng became chairman and general manager of Shengong Co., Ltd.
Shengong Co., Ltd. announced that the board of directors of the company elected Pan Liansheng as the chairman of the second board of directors, with a term of office from the date of adoption at the first meeting of the second board of directors to the date of expiration of the second board of directors. The Board of Supervisors of the Company elected Zhekai as the Chairman of the Second Board of Supervisors of the Company, with the term of office from the date of deliberation and approval at the first meeting of the Second Board of Supervisors to the date of expiration of the term of office of the Second Board of Supervisors.
In addition, the board of directors of the company agreed to hire Pan Liansheng as the general manager of the company and Yuan Xin as the deputy general manager, secretary of the board of directors and chief financial officer of the company.
Keda Manufacturing has received a total of 31,775,600 yuan from the government since April.
() Announcement: Since April 2021, the company and its subsidiaries have confirmed that the government subsidies related to income totaled 31,775,600 yuan, accounting for 11.17% of the company’s audited net profit attributable to shareholders of listed companies in 2020.
The shareholders of Yapu, SDIC Innovation and its concerted actions, have reduced their holdings by 1%.
() Announcement was issued. On August 30th, the company received a notice from SDIC Innovation and Cooperation Fund. From July 20th to August 30th, 2021, SDIC Innovation and Cooperation Fund reduced its holding of 5,142,200 shares of the company through block trading and centralized bidding, accounting for about 1% of the company’s total share capital. After this equity change, the proportion of shares held by SDIC Innovation and its concerted action cooperative fund decreased from 8.76% to 7.76%.
Minxin shares received a government subsidy of 4,293,400 yuan.
Minxin Co., Ltd. announced that the company and its wholly-owned subsidiaries Kunshan Lingke Sensing Technology Co., Ltd. (hereinafter referred to as "Kunshan Lingke"), Suzhou Desby Electronics Co., Ltd. (hereinafter referred to as "Desby") and its holding subsidiary Suzhou Xinyi Microelectronics Technology Co., Ltd. (hereinafter referred to as "Xinyi Micro") have received a total of 4,293,400 yuan in government subsidies related to income from January 1, 2021 to the disclosure date of this announcement.
Dongfeng shares hired Qiu as vice president and secretary of the board of directors of the group.
() Announce that Ms. Liu Wei, the former secretary of the board of directors of the company, has applied to the board of directors of the company for resignation as secretary of the board of directors for personal reasons, and will no longer hold any position in the company after resignation.
According to the nomination of Mr. Huang Xiaojia, the Chairman of the Board of Directors, and the audit by the Nomination Committee of the Board of Directors, the 10th meeting of the 4th Board of Directors of the Company held on August 29th, 2021 reviewed and approved the Proposal on Appointment of Group Vice President and Secretary of the Board of Directors, and agreed to appoint Mr. Qiu as the Group Vice President and Secretary of the Board of Directors of the Company until May 13th, 2023, which is the same as that of the current senior management. The independent directors of the company expressed their independent opinions and agreed to this proposal.
CITIC Jiantou completed the issuance of 3 billion yuan short-term financing bonds.
() It was announced that the 12th short-term financing bonds (Bond Pass) of the company in 2021 was issued on August 27th, 2021. The short name of the bonds is 21 China Securities Investment Co., Ltd. CP012BC, and the bond circulation code is 072100157. The actual issuance amount is 3 billion yuan, with a term of 62 days.
Huarong Holdings intends to terminate major asset restructuring.
Huarong Holdings announced that the company intends to terminate the purchase of 80% equity of Wuxi Shenrui Biological Products Co., Ltd. held by Sheng Qingsong and others by issuing shares and paying cash, and raise matching funds ("this reorganization"). The termination of this reorganization still needs to be reviewed and approved by the company’s relevant procedures. The company will hold a board meeting in the near future to consider matters related to the termination of this reorganization.
Since the start of this reorganization, the company and all parties concerned have actively promoted the work related to major asset reorganization. The intermediary agency hired by the company has conducted due diligence on the target company and related parties for nearly two months, and has conducted several rounds of discussion and communication with the counterparty and the target company on this reorganization. However, the company and the counterparty have great differences on the valuation of this restructuring, and the core terms cannot be agreed; At the same time, due to the epidemic situation, the due diligence process was slow, the relevant verification work was greatly affected, and the subsequent uncertainty increased.
Based on the above reasons, after careful research and analysis, the company and the counterparty believe that it will take a long time and have great uncertainty to continue to promote this restructuring plan at this stage, and both parties intend to stop planning this major asset restructuring.
The real controller of Zhijiang Biological, whose intraday share price is low, plans to increase its holdings.
On the evening of August 30, Zhijiang Bio announced that Shao Junbin, the actual controller and chairman of the company, intends to increase the company’s shares through centralized bidding transactions within six months from September 1, 2021. The total amount of shares to be increased this time is not less than RMB 10 million and not more than RMB 15 million.
For the purpose of increasing holdings, Zhijiang Bio’s announcement shows that Shao Junbin intends to increase his holdings of the company’s shares through centralized bidding transactions based on his confidence in the company’s future development and recognition of the company’s long-term investment value.
It is worth mentioning that Zhijiang Bio’s intraday share price once hit a new low of 50.4 yuan/share on August 30. As of August 30th, Zhijiang Bio received 50.5 yuan/share, down 4.59%.
According to financial data, Zhijiang Bio achieved an operating income of about 907 million yuan in the first half of this year, up 10.79% year-on-year; The corresponding attributable net profit was about 387 million yuan, a year-on-year decrease of 9.59%.
* There is no information that should be disclosed but not disclosed in the stock price change of ST Chengxing.
() It was announced that the deviation of the closing price increase of the company’s shares for three consecutive trading days on August 26th, 27th and 30th, 2021 was more than 15%, which was an abnormal fluctuation of stock trading.
After self-examination by the company and written consultation with the controlling shareholder and actual controller of the company, as of the disclosure date of this announcement, there is no significant information that should be disclosed but not disclosed.
There are no matters that should be disclosed but not disclosed in the stock price change of Red Star Development.
() Announced that the daily closing price of the company’s stock trading has deviated by more than 20% for three consecutive trading days on August 26th, 27th and 28th, 2021, which is an abnormal fluctuation of stock trading according to the relevant provisions of the Trading Rules of Shanghai Stock Exchange. After the company inquired about the controlling shareholder Red Star Group and the actual controller Qingdao SASAC, there are no matters that should be disclosed but not disclosed at present.
Tonghua dongbao: It is planned to sell 4% shares of Tebao Bio.
() On the evening of August 30th, it was announced that the company holds 30.06% of the shares of Tebao Bio, and the company intends to sell no more than 16.272 million shares of Tebao Bio by block trading or inquiry transfer, that is, no more than 4% of the current total share capital of Tebao Bio.
Tonghua dongbao: It is planned to sell 4% shares of Tebao Bio.
Tonghua dongbao announced on the evening of August 30th that the company holds 30.06% of the shares of Tebao Bio, and the company intends to sell no more than 16.272 million shares of Tebao Bio by block trading or inquiry transfer, that is, no more than 4% of the current total share capital of Tebao Bio.
Tonghua dongbao: It is planned to sell 4% shares of Tebao Bio.
Tonghua dongbao announced on the evening of August 30th that the company holds 30.06% of the shares of Tebao Bio, and the company intends to sell no more than 16.272 million shares of Tebao Bio by block trading or inquiry transfer, that is, no more than 4% of the current total share capital of Tebao Bio.
() As of June 30th, the accumulated power generation was 60,968,800 kWh, a year-on-year decrease of 59.04%.
Mei Yan Jixiang announced that as of June 30, 2021, Guangdong Meiyan Jixiang Hydropower Co., Ltd. (hereinafter referred to as "the company") and its holding subsidiary hydropower station have completed a total power generation of 60,968,800 kWh, a year-on-year decrease of 59.04%.
() Sign the Compensation Agreement for Demolition and Vacation.
Huida Sanitary Ware issued an announcement. According to the requirements of the demolition and vacating of plot No.1 in the urban-rural fringe transformation pilot project of Xihongmen Town, Daxing District, the company held the fourth meeting of the sixth board of directors on August 30, and reviewed and approved the "About signing"<拆除腾退补偿协议>Proposal ",agreed to 73.7792 million yuan as compensation for the demolition and retreat, demolition of the company’s land, houses and ground attachments located at No.28 Xihongmen Road, Daxing District, Beijing. The board of directors of the company authorized the management of the company to sign the compensation agreement and go through the relevant formalities. The company has signed the Compensation Agreement for Demolition and Retreat with Beijing Xinye Town Construction Management Investment Co., Ltd. (the vacating party designated by Daxing District Government) on the above matters.
Aofu Environmental hired Wu Xionghui as general manager.
Aofu Environmental Protection announced that Mr. Pan Jiqing, the chairman of the company, focused on corporate governance and strategic planning in order to better concentrate on the duties of the chairman, and nominated Mr. Wu Xionghui as the general manager of the company.
After full study, the board of directors of the company decided to appoint Mr. Wu Xionghui as the general manager of the company, and Mr. Pan Jiqing, the chairman of the company, no longer holds the post of general manager.
The repurchase rate of Jiangzhong Pharmaceutical reached 1%, costing 73.2727 million yuan.
() Announcement: As of August 27, 2021, the company has repurchased 6.3 million shares, accounting for 1% of the company’s total share capital. The highest transaction price is 11.88 yuan/share, the lowest price is 11.34 yuan/share, and the average repurchase price is 11.63 yuan/share, and the total amount paid is 73.2727 million yuan (excluding transaction fees such as stamp duty and trading commission). The company has completed the repurchase.
There is no significant information that should be disclosed but not disclosed in the stock price change of Longyuan Construction.
() Announce that the deviation of the closing price increase of the company’s shares in three consecutive trading days has exceeded 20%. After self-examination by the company, and confirmed to the controlling shareholder and actual controller, as of the disclosure date of the announcement, there is no significant information that should be disclosed but not disclosed.
Shanrong Industrial, the shareholder of Huachuang Yang ‘an, has reduced its shareholding by 6.2 million shares.
() Announcement was issued. On August 28th, 2021, Shanrong Industrial, the shareholder of the company, reduced its shareholding by 6,200,000 shares, accounting for 0.36% of the company’s total share capital, according to the Notice Letter on the Expiration of the Planned Reduction of Shares.
Jinan Hi-tech Subsidiary and its partners set up relevant subsidiaries.
() Announced that Jinan Jigao Hangu Industrial Development Co., Ltd. (hereinafter referred to as Jigao Hangu), a holding subsidiary of the company, invested 7 million yuan respectively to establish Qihe Jigao Hangu Urban Construction Investment Co., Ltd. (hereinafter referred to as Qihe Chengtou Company) and Qihe Jigao Hangu Industrial Development Co., Ltd. (hereinafter referred to as Qihe Chengtou Company)
Zhu Gang, supervisor of Lianrui New Materials, completed the plan to reduce the holding of 10,000 shares.
Lianrui New Materials announced that as of the date of this announcement, Mr. Jiang Bing, the company’s supervisor and core technician, has not reduced his holdings. Based on the confidence in the company’s future development prospects and judgment on the company’s value, combined with his own financial arrangements, and on July 12, 2021, Mr. Jiang Bing resigned as the employee representative supervisor and chairman of the board of supervisors of the third board of supervisors of the company. After comprehensive consideration, Mr. Jiang Bing decided to terminate the shareholding reduction plan ahead of schedule.
As of the date of this announcement, Mr. Zhu Gang, the supervisor of the company, reduced his shareholding by 10,000 shares through centralized bidding, accounting for 0.012% of the company’s total share capital. This shareholding reduction plan has been implemented.
There are no major events that should be disclosed but not disclosed in the stock price change of 3D shares.
() It was announced that the daily closing price of the company’s stock rose by more than 20% in three consecutive trading days on August 26th, 27th and 30th, 2021, which is an abnormal fluctuation of stock trading according to the relevant provisions of the Trading Rules of Shanghai Stock Exchange. After the company’s self-examination and verification with the controlling shareholder and actual controller of the company, as of the disclosure date of the announcement, the company’s operation is normal, and there are no major matters that should be disclosed but not disclosed.
State Grid ICT elected Yang Min as employee supervisor.
() Announcement was issued. On August 30, 2021, the company received the Resolution on Electing Staff and Supervisors of the Eighth Board of Supervisors of the Company from the Trade Union Committee. On August 27, 2021, the company held the third staff meeting in 2021, and elected Ms. Yang Min as the staff and supervisors of the Eighth Board of Supervisors of the Company. The term of office was the same as that of the Eighth Board of Supervisors.
Nuoli intends to participate in the establishment of Changxing Shangdianke Robot Equity Investment Fund.
() Announcement. Recently, the company signed a partnership agreement with Dianke Construction Engineering Co., Ltd., and agreed to jointly initiate the establishment of Changxing Shangdike Robot Equity Investment Partnership (Limited Partnership). The fund manager is Dianke Capital. According to the above agreement, the subscribed amount of Nuoli shares is 72.5 million yuan, accounting for 29% of the total subscribed capital of the fund. The fund mainly focuses on high-quality target enterprises in the middle and late stages of development in related industries such as robots and intelligent manufacturing.
The main purpose of the company’s participation in the investment fund this time is to expand the investment field through professional management and market-oriented operation, and at the same time, to promote the establishment of cooperation between other business sectors of Nuoli Co., Ltd. and the target companies to be invested by the fund in the future, and accelerate the industrial upgrading and growth of the company.
Shanghai Construction Engineering Investment Co., Ltd. plans to spend 90 million yuan to participate in the robot fund.
() Announcement. Recently, Shanghai Construction Engineering Group Investment Co., Ltd. (hereinafter referred to as "Construction Engineering Investment"), a wholly-owned subsidiary of the company, and Huzhou Dianke Construction Engineering Equity Investment Partnership (Limited Partnership) signed the "Changxing Shangdian Robot Equity Investment Partnership (Limited Partnership)" to jointly establish Changxing Shangdian Robot Equity Investment Partnership (Limited Partnership) (hereinafter referred to as "Robot Fund").
According to the agreement, construction engineering investment, as a limited partner LP, invested 90 million yuan in the robot fund, accounting for 36% of the total subscribed capital of the fund and 40% of the total subscribed capital in the first phase. Jiaxing Jianyi Investment Co., Ltd., a wholly-owned subsidiary of Construction Engineering Investment Co., Ltd., as a limited partner LP, invested RMB 4 million in Huzhou Dianke Construction Engineering Equity Investment Partnership (limited partnership) (general partner GP of Robot Fund), accounting for 40% of the total subscribed capital of the partnership and 25% of the total subscribed capital in the first phase.
It is reported that this fund mainly focuses on high-quality target enterprises in the middle and late stages of development in related industries such as robots and intelligent manufacturing, focusing on investment opportunities such as intelligent manufacturing, special robots and construction robots.
According to the announcement, by investing in the robot fund, the company will share resources and complement each other with relevant parties of the industrial fund, share high-quality investment opportunities in the field of robots and special equipment, and obtain certain financial investment income through industrial investment. This fund will promote the application and promotion of robots in the construction field, help the company to build digitally and intelligently in the construction field, and help the company to transform and develop.
Guangzhou Port intends to agree to Maoming Guanggang to implement the construction of berths 3# and 4# of Maoming Bohe New Port General Wharf.
() Announced that in order to meet the needs of wharf construction and business development of Maoming Guanggang Wharf Co., Ltd. (hereinafter referred to as "Maoming Guanggang"), the company intends to agree to implement the construction of berths 3# and 4# of Maoming Bohe New Port General Wharf, with a total investment of 918 million yuan.
It is reported that Maoming Guanggang was jointly established by Guangdong Ganghang Investment Co., Ltd., a wholly-owned subsidiary of the company, and maoming port Group Co., Ltd., of which Guangdong Ganghang Investment Co., Ltd. holds 70% of the shares and maoming port Group Co., Ltd. holds 30% of the shares, and is responsible for the construction and operation of the general wharf project in Bohe New Port Area, maoming port.
According to the announcement, the project is the No.3 and No.4 berth project of Maoming Bohe New Port General Terminal Phase II, which plays an important role in further improving the berth capacity of Maoming Guanggang Terminal Co., Ltd., which is controlled by the company, and meeting the growth needs of port loading and unloading business. After the completion of the project, the business of Maoming Guanggang Wharf Co., Ltd. will further develop on a large scale, which is conducive to the company’s competitiveness and sustainable development.
Wanhua Chemical’s MDI listing price in China in September has not changed compared with that in August.
() Announcement: Since September, 2021, the listing price of the company’s China polymeric MDI distribution market is 20,600 yuan/ton (unchanged from August), and the listing price of the direct selling market is 20,600 yuan/ton (unchanged from August); The listing price of pure MDI is 23,800 yuan/ton (no change compared with August).
Shanghai Construction Engineering’s net profit in the first half of the year was 1.374 billion, and its real estate business revenue was 2.121 billion.
On August 30, Shanghai Construction Engineering Group Co., Ltd. announced that in the first half of 2021, its new contract was 211.831 billion yuan, a year-on-year increase of 26.65%; Realized operating income of 135.214 billion yuan, a year-on-year increase of 29.83%; The net profit of returning to the mother was 1.374 billion yuan, a year-on-year increase of 10.52%.
Shanghai Construction Engineering Co., Ltd. said that during the period, the accumulated new contracts completed 48.14% of the total annual new contract target. Among them, the newly signed contracts in Shanghai market totaled 119.098 billion yuan, accounting for 56.22%; The cumulative number of new contracts signed in other provinces and cities was 88.042 billion yuan; A total of 4.691 billion yuan of new contracts were signed in overseas markets.
In the first half of the year, six emerging businesses in Shanghai, such as urban renewal, water conservancy and water affairs, ecological environment, industrial construction, construction services and new infrastructure, signed new contracts of 11.830 billion yuan, 5.953 billion yuan, 2.425 billion yuan, 8.423 billion yuan, 1.832 billion yuan and 905 million yuan respectively.
According to Viewpoint Real Estate New Media, during the reporting period, Shanghai Construction Engineering achieved an operating income of 2.121 billion yuan in real estate development business, up 1.57% year-on-year, accounting for 1.57% of the current revenue, with a gross profit margin of 11.72%.
Xinwufeng plans to set up a joint venture company to operate sow farm.
() Announced that in order to promote the development of the company’s pig industry, the company plans to jointly invest with Hunan Tianze Enterprise Management Partnership (hereinafter referred to as Tianze Partnership) to establish Phoenix New Wufeng Animal Husbandry Co., Ltd. (hereinafter referred to as "Phoenix New Wufeng"). The registered capital of Phoenix New Wufeng is 50 million yuan, of which, Xinwufeng contributes 35 million yuan in cash, accounting for 70% of the registered capital; Tianze Partnership contributed RMB 15 million in cash, accounting for 30% of the registered capital.
After the establishment, Phoenix New Wufeng plans to lease the newly-built sow farm with a stock scale of 10,800 in Phoenix Zhongsheng for operation. The rental field is located in Tuojiang Town, Fenghuang County, Hunan Province, with a good geographical environment, superior surrounding breeding environment, convenient roads and superior biological epidemic prevention conditions. The project adopts the lease operation mode, and the construction investment mainly includes the cost of introducing adult sows, the start-up and preliminary work expenses of the new company, the estimated investment expenses of the first year’s working capital, the rental expenses of the farm, the interest expenses during the construction period, etc. The total investment of the project is 135 million yuan.
The company said that the introduction of Tianze partnership in this project can combine the company’s specialized breeding technology, efficient production and operation with Tianze partnership’s good peripheral relationship and coordination ability, which is conducive to the stable development of aquaculture. After the completion of this project, the company will increase the supply of piglets, reduce production costs, improve production quality and production efficiency.
1,803,700 restricted shares of Jinpan Technology were listed and circulated on September 9.
Jinpan Technology announced that the restricted shares were released from circulation on September 9, 2021. The number of restricted shares listed and circulated this time was 1,803,700, and the restricted sale period was June.
Transfer assets between Rizhao Port and its wholly-owned subsidiaries.
() Announcement: In order to make the production organization smoother, the management system more efficient and the customer service better, the company held the eighth meeting of the seventh board of directors and the seventh meeting of the seventh board of supervisors on May 28, 2021, and deliberated and passed the Proposal on Adjustment of Production Layout. According to the adjustment of production layout, the company will transfer some assets and debts to Rizhao Port Lanshan Port Co., Ltd. (hereinafter referred to as "Lanshan Company") at the net book value based on April 30, 2021.
() It is proposed to grant 777,500 reserved restricted shares to the incentive object at a grant price of 9.95 yuan/share.
Taijing Technology announced that the third meeting of the fourth board of directors of the company reviewed and approved the Proposal on Granting Reserved Restricted Shares to Incentive Objects on August 30, 2021. The board of directors of the company agreed to grant 777,500 restricted shares to 83 incentive objects at a grant price of 9.95 yuan/share, and the grant date of reserved restricted shares was September 1, 2021.
There are no undisclosed major events in the stock price change of Guosheng Zhike.
Guosheng Zhike announced that the deviation of the closing price of the company’s stock trading within three consecutive trading days (August 26, August 27 and August 30, 2021) has reached 30%, which is an abnormal fluctuation of stock trading.
After self-examination by the company and written letter to the controlling shareholder and actual controller for verification, as of the disclosure date of this announcement, there are no major matters about the company that should be disclosed but not disclosed, and there are no major matters in the planning stage. At present, the daily operation of the company is normal, and no major changes have taken place.
In order to lay out the core logistics resources, Jianfa Co., Ltd. plans to set up Shangzhou Logistics with Xiamen Airlines and other expenses of 1 billion yuan.
() Announcement, the company plans to jointly invest in the establishment of Shangzhou Logistics with related parties Xiamen Airlines and Zongteng Network, with a registered capital of 1 billion yuan, of which the company contributes 501 million yuan in cash, accounting for 50.1% of the registered capital; Xiamen Airlines invested 379 million yuan in buildings, equipment and facilities, land use rights and cash, accounting for 37.9% of the registered capital. Zongteng Network contributed 120 million yuan in cash, accounting for 12% of the registered capital.
The announcement shows that the above investment will help the company to lay out its core logistics resources and promote the development of cross-border e-commerce and other consumer goods supply chain business.
Xiamen Trust, the shareholder of ST Hanye, plans to reduce its holdings by no more than 31.29 million shares.
() Announcement, the company recently received () (Shanghai) Asset Management Co., Ltd. (on behalf of "Qilu Asset Management Puyin No.2203 Directional Asset Management Plan", and the client of Qilu Asset Management Puyin No.2203 Directional Asset Management Plan is Xiamen International Trust Co., Ltd. (on behalf of "Xiamen Trust-Huijin No.1628"). Xiamen Trust-Huijin No.1628 plans to reduce its holdings of the company’s shares by no more than 31.29 million shares from September 27th, 2021 to December 26th, 2021, that is, no more than 1% of the company’s total shares, and no more than 1% of the total share capital within 90 consecutive days.
Ma Hengjun, deputy general manager of Ou Lin Bio, completed the plan to increase the holding of 209,100 shares.
Ou Lin Bio announced that as of the disclosure date of this announcement, Mr. Ma Hengjun, the deputy general manager of the company, has accumulated 209,100 shares of the company, accounting for 0.05% of the company’s total share capital, with an increase of 6,060,600 yuan. After this increase, Mr. Ma Hengjun’s direct shareholding accounts for 1.20% of the company’s total share capital. As of the disclosure date of this announcement, Mr. Ma Hengjun’s plan to increase his holdings has been implemented.
In the first half of the year, ST Anxin needs to accrue the impairment loss of financial assets of about 121 million yuan.
() Announcement. According to preliminary calculation, the company needs to accrue about 121 million yuan of credit impairment loss and fair value change income of financial assets in the first half of 2021, which mainly includes about 102 million yuan of debt investment assets impairment reserve, about 12 million yuan of fair value change income of trading financial assets, about 13 million yuan of impairment loss of receivables and other receivables assets and about 18 million yuan of expected credit loss.
Yu Renrong, the controlling shareholder of Weir, intends to reduce its holdings by no more than 7.9 million shares.
() Announcement, due to personal financial needs, Mr. Yu Renrong, the controlling shareholder of the company, plans to reduce the company’s shares by no more than 900,000 shares through centralized bidding and no more than 7,000,000 shares through block trading within six months after the disclosure of this announcement, with a total reduction of no more than 7,900,000 shares, accounting for 0.91% of the company’s current total share capital.
Jingyuan Environmental Protection appointed Xu Xiaoqin as the representative of securities affairs.
Jingyuan Environmental Protection issued an announcement. On August 30, 2021, the company held the 10th meeting of the third board of directors, and reviewed and approved the Proposal on Appointment of Securities Affairs Representatives. The board of directors agreed to appoint Mr. Xu Xiaoqin as the company’s securities affairs representative to assist the secretary of the board of directors in his daily work. The term of office shall be from the date of deliberation and approval at this board meeting to the date of expiration of the third board of directors.
Earth Bear plans to permanently replenish its working capital with over-raised funds of 44.8 million yuan.
Dadixiong announced that the company plans to use the over-raised funds of RMB 44.8 million to permanently supplement the working capital. The total amount of over-raised funds of the company is 149 million yuan, and the amount to be used for permanently replenishing working capital accounts for 29.97% of the total amount of over-raised funds.
Many directors of Longsoft Technology plan to reduce their holdings by no more than 849,200 shares.
Longruan Technology announced that Mr. Ren Yongzhi, director, vice chairman, deputy general manager and core technician, Mr. Guo Bing, director, deputy general manager and core technician, Mr. Lei Xiaoping, deputy general manager and core technician, and Mr. Wei Xiaoping, chairman of the board of supervisors and core technician, plan to reduce their holdings of the company’s shares by centralized bidding or block trading, with a total reduction of no more than 849,200 shares.
Zhangjiang Hi-Tech subsidiary plans to transfer some assets of RMB 152 million.
() Announced that Zhangjiang Collector, a wholly-owned subsidiary of the company, intends to transfer 10 real estates (corresponding to the land use right and its buildings, structures and ancillary facilities and equipment) held at No.1761 Zhangdong Road, Pudong New Area, Shanghai, with a construction area of 4734.37 square meters and a transfer price of 152 million yuan. This asset transfer will increase the income and profit of the company’s main business and increase the operating cash inflow of listed companies. It is estimated that this asset transfer will achieve a net profit of 50 million yuan.
Ling Gang shares: It is planned to increase the registered capital of its subsidiary Baoguo Company by 300 million yuan.
() It was announced on the evening of August 30th that the company plans to increase the registered capital of its wholly-owned subsidiary Ling Gang Beipiao Baoguo Iron Mine Co., Ltd. (hereinafter referred to as Baoguo Company) by 300 million yuan with free capital, and start the construction of "green mine" and "intelligent mine" as soon as possible.
Ling Gang said that since 2020, the price of imported iron ore has continued to rise, and the domestic iron ore market has also continued to improve. Compared with imported iron ore, the domestic iron ore price advantage is obvious. At present, the state is also encouraging mining enterprises with standardized management to speed up the construction of "green mines". In view of the fact that Baoguo Company is implementing the -190m project in Tiedanshan mining area and the project of converting open pit mining to underground mining in Bianjiagou mining area, and plans to start the construction of "green mines" and "smart mines" during the Tenth Five-Year Plan period, the capital demand is large, and it is difficult for Baoguo Company to meet the future capital demand by its own operation and accumulation.
Ling Gang Co., Ltd. said that this investment is made to meet the capital needs of Baoguo Company, which is conducive to accelerating the construction of the -190m project in Tiedanshan Mining Area and the open-pit to underground mining project in Bianjiagou Mining Area of Baoguo Company, seizing market opportunities, achieving production and efficiency as soon as possible, and providing strong support for the company’s low-cost strategy; In addition, the construction of "green mines" and "smart mines" should be started as soon as possible to realize green manufacturing, intelligent manufacturing and sustainable development.
Xinwufeng plans to set up Miluo Xinwufeng to operate sow farm.
Xinwufeng announced that in order to promote the development of the company’s pig breeding, the company plans to jointly establish Miluo Xinwufeng Animal Husbandry Co., Ltd. (referred to as Miluo Xinwufeng) with Yueyang Yongyi Ecological Breeding Co., Ltd. (referred to as Yueyang Yongyi). The registered capital of Miluo Xinwufeng is 30 million yuan, of which: the company contributed 21 million yuan in cash, accounting for 70% of the registered capital; Yueyang Yongyi contributed RMB 9 million in cash, accounting for 30% of the registered capital.
After the establishment, Miluo Xinwufeng intends to lease the newly-built sow farm with 6,000 heads in Hunan Tianhan Animal Husbandry Development Co., Ltd. (referred to as "Tianhan Animal Husbandry") for operation. The rental field is located in Fengcang Village, Shendingshan Town, Miluo City, Yueyang City, with a good geographical environment, superior surrounding breeding environment, convenient roads and superior biological epidemic prevention conditions. This project adopts the mode of renting farms. The construction investment mainly includes the cost of introducing adult sows, the start-up and preliminary work expenses of new companies, the estimated investment expenses of the first year’s working capital, the rental expenses of farms (the first four years’ rent) and the interest expenses during the construction period. The total investment of the project is 71,805,800 yuan.
The company said that the introduction of Yueyang Yongyi into this project can combine the company’s specialized breeding technology and efficient production operation with the breeding experience and coordination ability of Yueyang Yongyi management team, which is conducive to the stable development of the breeding industry. After the completion of this project, the company will increase the supply of piglets, reduce production costs, improve production quality and production efficiency.
Since 2021, Zhongguang Natural Selection has received a total of 11,211,200 yuan from the government.
() Announcement: From January 1, 2021 to the date of this announcement, the company and its subsidiaries Changsha Zhongtian Selective Purchase Information Technology Co., Ltd., Hunan Million Fans Culture Technology Co., Ltd. and Jirui Vision (Hunan) Investment Management Co., Ltd. successively received a total of 9 government subsidies, with a cumulative amount of 11,211,200 yuan, all of which were related to income.
There is no significant undisclosed information about Dr. Peng’s share price change.
() It was announced that the deviation of the closing price of the company’s shares in three consecutive trading days on August 26th, 27th and 30th, 2021 was more than 20%, which constituted the abnormal fluctuation of stock trading as stipulated in the Trading Rules of Shanghai Stock Exchange. After self-examination by the company and written confirmation to the controlling shareholder and actual controller, there is no significant information that should be disclosed but not disclosed by the company, its controlling shareholder and actual controller.
In order to seize the market opportunity, Huijia Times plans to acquire related commercial real estate developed and constructed by related parties.
() Announcement: Fukang Huijia Times Department Store Co., Ltd. ("Fukang Huijia"), a wholly-owned subsidiary of the company, plans to purchase the commercial real estate developed and constructed by fukang city Huijia Real Estate Development Co., Ltd. ("Fukang Huijia Real Estate") at the intersection of Bofeng West Road and Nanhua Road in fukang city, from the ground floor to the ground floor, with a total construction area of 34,584.31 square meters.
The announcement shows that Fukang Huijia Real Estate is an enterprise actually controlled by Pan Jinhai, the controlling shareholder and actual controller of the company. The purpose of this transaction is to consolidate the competitive advantage in the regional market, seize the market opportunities, fill the gaps in the regional market and further improve the strategic layout of the company.
The secretary of the board of directors of Jinling Hotel was changed to Liu Yuxin.
() Announcement was issued. The third meeting of the seventh board of directors of the company was held on August 27, 2021, and the Proposal on Changing the Secretary of the Board of Directors of the Company was reviewed and approved. Mr. Wang Hao resigned as secretary of the board of directors and assistant to the general manager for personal reasons, and the board of directors agreed to Mr. Wang Hao’s resignation application.
On the nomination of Ms. Li Xi, the Chairman of the Board of Directors, the Board of Directors appointed Mr. Liu Yuxin as the Secretary of the Board of Directors of the Company for the same term as that of the current Board of Directors.
Yihuatong plans to issue H shares and list them in Hong Kong.
Yihuatong announced that on August 30, 2021, the company held the 24th meeting of the second board of directors, which reviewed and approved the Proposal on the Company’s Issuance of H Shares, Listing in Hong Kong, and Turning into a Company Limited by Share Offering Abroad and other related proposals.
Up to now, the company is actively discussing with relevant intermediaries about the relevant work of issuing H shares and listing on the Hong Kong Stock Exchange. The specific details of this issuance and listing have not yet been determined. At the same time, the company is actively revising its articles of association and related rules in accordance with the Necessary Clauses of the Articles of Association of Companies Listed Abroad, the Letter on Supplementary Amendments to the Articles of Association of Companies Listed in Hong Kong, and the Listing Rules of the Stock Exchange of Hong Kong Limited.
The controlling shareholder and concerted parties of Fuda Alloy intend to reduce their holdings by no more than 3.44%.
() Announcement: Wang Dawu, the controlling shareholder of the company, intends to reduce the holding of no more than 4,128,600 shares of the company through centralized bidding and/or block trading, accounting for 3% of the company’s total share capital. Its concerted actions, Qian Chaobin and Li Fengfei, plan to reduce their holdings by no more than 428,700 shares and 176,400 shares by centralized bidding, with the reduction ratio not exceeding 0.31% and 0.13% of the company’s total share capital respectively.
Huili Assets, the shareholder of Xinghu Technology, plans to reduce its holdings by no more than 14.78 million shares.
() Announce that Huili Assets plans to reduce its shares in Xinghu Technology by centralized competitive bidding and other ways permitted by laws and regulations, according to the Notice Letter of August 30, 2021 issued by Shenzhen Great Wall Huili Assets Service Enterprise (Limited Partnership) (hereinafter referred to as Huili Assets). Among them, no more than 14.78 million shares will be reduced by centralized bidding within 6 months after 15 trading days from the date of the announcement of the reduction plan, that is, no more than 2% of the company’s total share capital. The reduction price is determined according to the market price at the time of reduction.
Yihuatong appointed Li Feiqiang as Deputy General Manager.
Yihuatong announced that the company held the 24th meeting of the second board of directors on August 30th, 2021. The meeting reviewed and passed the Proposal on Appointment of Senior Managers. Upon nomination by the general manager of the company and review by the nomination committee of the board of directors, the board of directors agreed to appoint Mr. Li Feiqiang as the deputy general manager of the company, with the term of office from the date of deliberation and approval at this meeting to April 28th, 2022.
Tiandiyuan hired Yu Ling as the chief financial officer.
() Announcement, the board of directors of the company recently received a written resignation report from Mr. Wang Naibin, the company’s chief financial officer, who applied to resign as the company’s chief financial officer due to job transfer. After his resignation, Mr. Wang Naibin will no longer hold any position in the company, and his resignation will not affect the normal production, operation and management of the company.
In order to ensure the normal operation of the company, according to the relevant provisions of the Company Law and Articles of Association, the nomination committee of the board of directors of the company reviewed and approved the qualifications of Ms. Ling, and agreed to appoint Ms. Yu Ling as the company’s chief financial officer. The term of office will be from the date of deliberation and approval by the board of directors to the expiration of the term of the ninth board of directors of the company.
The shareholding ratio of Diwei Investment, the shareholder of Kaisai Bio, reached 1.01%, and its shareholding decreased to 4.62%.
Kaisai Bio announced that Wuxi Dewei Investment Partnership (Limited Partnership) ("Dewei Investment"), a shareholder of the company, reduced its shareholding by 4.2 million shares on August 30, 2021, with a reduction ratio of 1.01%, and its shareholding ratio decreased from 5.63% to 4.62%.
Jianghang Equipment: Liu Zhen resigned as supervisor.
Jianghang Equipment announced that the company’s board of supervisors recently received the resignation application from Ms. Liu Zhen, the company’s supervisor. Due to personal job adjustment, Ms. Liu Zhen applied to resign as the supervisor of the first board of supervisors of the company. After Ms. Liu Zhen resigns as a supervisor, she will not hold any post in the company.
On August 30, 2021, the company held the 10th meeting of the first Board of Supervisors, deliberated and passed the Proposal on Resignation of Supervisors and Nominating Candidates for Supervisors, and agreed to nominate Mr. Hu Zhongjun as the candidate for the first Board of Supervisors, with the term of office from the date of deliberation and approval by the shareholders’ meeting of the company to the date of expiration of the term of the first Board of Supervisors.
Gu Jia Jia ju plans to spend about 1.2 billion yuan to build a southwest production base to shorten the transportation cycle.
() Announcement: On August 30, 2021, the company signed the Project Investment Agreement with the People’s Government of jiangjin district, Chongqing, and plans to invest about 1.2 billion yuan to build the southwest production base project of Gujia Home. The company will register a wholly-owned or controlled project production and sales company with independent legal personality in jiangjin district as the main body of this project.
According to the announcement, the project covers an area of about 294 mu, and is expected to start in the first quarter of 2022. The construction period of the project is 20 months, and it is expected to be completed and put into operation before the end of 2023. When the overall project reaches the outline, it is expected to realize an operating income of about 2.5 billion yuan. After-tax internal rate of return reached 11.79%, and the static investment payback period (including construction period) was 7.37 years.
It is reported that the layout of the production base in Southwest China will help shorten the transportation cycle, reduce production costs and increase market expansion in Southwest China. The products of this project mainly cover sofas, soft beds, mattresses and other products. The landing of the project can meet the company’s expansion and extension of all categories of home furnishing in various regions of the country, which is an important step in the continuous promotion of the company’s expansion strategy.
Fuda Alloy’s controlling shareholder and concerted parties intend to reduce their shares.
On the evening of August 30, Fuda Alloy disclosed that the company recently received a letter of reduction plan from its controlling shareholder Wang Dawu and his fellow pedestrians Qian Chaobin and Li Fengfei.
Specifically, Wang Dawu intends to reduce his holdings by no more than 4,128,600 shares of the company through centralized bidding and/or block trading, accounting for 3% of the total share capital of listed companies; Qian Chaobin and Li Fengfei plan to reduce their holdings by no more than 428,700 shares and 176,400 shares respectively, and the reduction ratio shall not exceed 0.31% and 0.13% of the total share capital of listed companies respectively.
It should be pointed out that since May this year, the share price of Fuda Alloy has ushered in a wave of surge. According to statistics, during the 79 trading days from May 11 to August 30, the cumulative increase of Fuda alloy range reached 40.17%, and the company’s share price hit a high of 16.14 yuan/share in intraday trading on August 29.
Jianfa shares: It is planned to set up Shangzhou Logistics with Xiamen Airlines and others to spend 1 billion yuan.
On August 30, the financial network announced that the company plans to jointly invest with related parties Xiamen Airlines and Zongteng Network to set up Shangzhou Logistics with a registered capital of 1 billion yuan, of which the company contributed 501 million yuan in cash, accounting for 50.1% of the registered capital.
Gu Jia Home Furnishing: Supervisor Zhou Weiyu resigned.
Gu Jia Home announced that the company’s board of supervisors recently received a written resignation report from supervisor Zhou Weiyu, who applied to resign as a supervisor of the fourth board of supervisors of the company due to personal work changes. After resigning, Zhou Weiyu will no longer hold other positions in the company.
In view of the fact that the number of supervisors of the company will be lower than the legal minimum after Zhou Weiyu’s resignation, in order to ensure the normal operation of the board of supervisors, according to the relevant regulations, Zhou Weiyu’s resignation application will take effect after the company’s shareholders’ meeting elects a new supervisor to fill the vacancy, before which Zhou Weiyu still needs to continue to perform his duties as a supervisor.
The Fourth Meeting of the Fourth Board of Supervisors of the Company deliberated and passed the Proposal on By-election of Supervisors, and nominated Jin Darong as the candidate for the shareholder representative supervisor of the Fourth Board of Supervisors of the Company, with the term of office from the date of deliberation and approval by the shareholders’ meeting to the date of expiration of the term of the Fourth Board of Supervisors. This proposal still needs to be submitted to the company’s shareholders’ meeting for consideration.
Bohai Fund, a shareholder of Chengdu Bank, intends to reduce its holdings by no more than 36.1225 million shares.
() Announced that Bohai Industrial Investment Fund Management Co., Ltd., the shareholder of the company, on behalf of Bohai Industrial Investment Fund (hereinafter referred to as "Bohai Fund"), plans to reduce its shares in the company by centralized bidding or block trading within three months after three trading days from the date of announcement of this reduction plan, accounting for 1.00% of the total shares of the company.
Dadixiong plans to increase capital with the northern rare earth to the associated company to ensure the supply of rare earth raw materials.
Dadixiong announced that the company plans to increase the capital of its associate company (Anhui) Permanent Magnet Technology Co., Ltd. ("North Rare Earth Anhui Permanent Magnet") by RMB 36.144 million in cash, and China North Rare Earth (Group) High-tech Co., Ltd. ("North Rare Earth", stock code: 600111.SH) will increase the capital in cash in the same proportion. After the completion of this capital increase, the company holds 40% equity of North Rare Earth Anhui Permanent Magnet, and the proportion of equity between the company and North Rare Earth remains unchanged.
The announcement shows that the purpose of this investment is to deepen the division of labor and cooperation between the company and the northern rare earth Anhui permanent magnet, give play to their respective advantages and industrial synergy, and continue to improve the industrial layout and ensure the supply of rare earth raw materials through this investment while obtaining investment income.
Wenfeng shares plans to spend 50 million yuan to 100 million yuan to buy back shares.
() Announce that the company plans to spend 50 million yuan to 100 million yuan to buy back shares at a price of no more than 4.40 yuan/share, and the repurchased shares will be used for the later implementation of the employee stock ownership plan.
Dadixiong plans to increase capital with the northern rare earth to the associated company to ensure the supply of rare earth raw materials.
Dadixiong announced that the company plans to increase capital of 36.144 million yuan in cash to its associate company North Rare Earth (Anhui) Permanent Magnet Technology Co., Ltd. ("North Rare Earth Anhui Permanent Magnet"), and China North Rare Earth (Group) High-tech Co., Ltd. ("North Rare Earth", stock code: 600111.SH) will increase capital in cash in the same proportion. After the completion of this capital increase, the company holds 40% equity of North Rare Earth Anhui Permanent Magnet, and the proportion of equity between the company and North Rare Earth remains unchanged.
The announcement shows that the purpose of this investment is to deepen the division of labor and cooperation between the company and the northern rare earth Anhui permanent magnet, give play to their respective advantages and industrial synergy, and continue to improve the industrial layout and ensure the supply of rare earth raw materials through this investment while obtaining investment income.
() The second phase of stock options and restricted stock incentive plan awarded the restricted stock conditional achievement in the second unlocking period for the first time.
Zhichun Technology announced that the company held the seventh meeting of the fourth board of directors on August 30, 2021, and deliberated and passed the Proposal on the Achievement of the Second Unlocking Conditions for Restricted Stocks Granted by the Company’s Second Equity Incentive, agreeing to unlock 30% of the total restricted stocks granted for the first time in the second equity incentive. The number of incentive targets that meet the conditions for lifting the restricted sales this time is 51, and the number of restricted shares that can be lifted this time is 245,200 shares.
Tonghua dongbao plans to sell no more than 16.272 million shares of Tebao Bio.
Tonghua dongbao announced that the company intends to sell Xiamen Tebao Bio-engineering Co., Ltd. (stock code: 688278, referred to as "Tebao Bio") shares (unrestricted shares) by way of block trading or inquiry transfer, which is no more than 16.272 million shares, that is, no more than 4% of the current total share capital of Tebao Bio. The selling price is determined according to the market price at the time of reduction.
Tonghua dongbao plans to sell no more than 16.272 million shares of Tebao Bio.
Tonghua dongbao announced that the company intends to sell Xiamen Tebao Bio-engineering Co., Ltd. (stock code: 688278, referred to as "Tebao Bio") shares (unrestricted shares) by way of block trading or inquiry transfer, which is no more than 16.272 million shares, that is, no more than 4% of the current total share capital of Tebao Bio. The selling price is determined according to the market price at the time of reduction.
There is no information that should be disclosed but not disclosed in the stock price change of Yunsai Zhilian.
() It was announced that the deviation of daily closing price of A-shares in the company exceeded 20% for three consecutive trading days on August 26th, 27th, and 30th, 2021, which constituted the abnormal fluctuation of stock trading as stipulated in the Trading Rules of Shanghai Stock Exchange.
After the company’s self-examination and consultation with the controlling shareholder and actual controller, as of the disclosure date of this announcement, there is no information that should be disclosed but not disclosed by the company and the controlling shareholder and actual controller.
Huatong Cable elected Zhang Wendong as the chairman and appointed Zhang Shujun as the general manager.
() Announcement: On August 30, 2021, the board of directors and the board of supervisors of the company deliberated and passed several proposals, electing Zhang Wendong as the chairman, Ma Hongrui as the chairman of the board of supervisors, Zhang Shujun as the general manager, Luo Xiaoyu as the chief financial officer and secretary of the board of directors, and Zhang Baolong, Cheng Wei and Hu Deyong as the deputy general managers.
Shao Junbin, the actual controller of Zhijiang Bio, plans to increase the company’s shares by 10 million yuan to 15 million yuan.
Zhijiang Bio announced that Mr. Shao Junbin, the actual controller and chairman of the company, based on his confidence in the company’s future development and recognition of the company’s long-term investment value, plans to increase his shareholding in the company through centralized bidding within six months from September 1, 2021. The total amount of shares to be increased this time is not less than RMB 10 million and not more than RMB 15 million.
Shanshi Net Branch appoints Tang Yan as the representative of securities affairs.
Shanshi NetScience announced that the board of directors of the company reviewed and approved the Proposal on Appointing Securities Affairs Representatives on August 30, 2021, and the board of directors agreed to appoint Tang Yan as the company’s securities affairs representative to assist the secretary of the board of directors in carrying out related work. The term of office will start from the date of review and approval by the board of directors until the expiration of the first board of directors of the company.
Gravitation Media appoints Mu Yabin as the representative of securities affairs.
() Announced that the company held the fourth meeting of the fourth board of directors on August 30, reviewed and passed the Proposal on Appointing the Company’s Securities Affairs Representative, and agreed to appoint Ms. Mu Yabin as the securities affairs representative, with the term of office from the date of appointment by the board of directors to the expiration of the fourth board of directors of the company.
Tieliu intends to acquire relevant assets of Express Sifang and Express Guolian to broaden sales channels.
() Announcement: Leishi Technology (Hangzhou) Co., Ltd. ("Leishi Technology"), a wholly-owned subsidiary of the company, signed the Acquisition Agreement with Yuntong Sifang Auto Parts Supply Chain Co., Ltd. ("Yuntong Sifang") and Fujian Yuntong Guolian Auto Parts Co., Ltd. ("Yuntong Guolian") on August 27, 2021. According to the arrangement of the agreement, Leishi Technology intends to acquire the operating assets involved in the main business of the counterparty, and 100% equity of Guangdong Yuntong Sifang Auto Parts Co., Ltd. ("Yuntong Auto Parts") and 100% equity of Fujian Guolian Auto Parts Co., Ltd. ("Guolian Auto Parts") held by the counterparty (collectively referred to as the "Target Company").
The transaction is paid in cash, and the estimated transaction price is no more than 180 million yuan (the final price is subject to the actual delivery date price). Upon completion of this transaction, Yuntong Auto Parts and Guolian Auto Parts will become wholly-owned subsidiaries of Leishi Technology, a subsidiary of the company.
It is reported that the company is a large-scale manufacturing enterprise in the field of automobile core transmission parts segmentation, and Guolian Auto Parts and Yuntong Auto Parts are large-scale auto parts intelligent service enterprises accumulated in the automotive aftermarket for decades, with advanced intelligent supply chain and perfect distribution network, and complete product categories, which can provide online and offline multi-dimensional one-stop automotive intelligent services and experiences for automotive aftermarket customers, especially commercial vehicle aftermarket customers.
The announcement shows that the company’s acquisition of Guolian Auto Parts and Yuntong Auto Parts through its subsidiary Leishi Technology Platform is conducive to the exchange of resources, which is conducive to broadening sales channels, expanding the sales scale of the company and increasing the market share of the company’s products.
Jianfa shares: 501 million yuan to participate in air cargo transportation enterprises.
Jianfa announced on the evening of August 30th that it plans to jointly invest with Xiamen Airlines and Zongteng Network to establish Shangzhou Logistics with a registered capital of 1 billion yuan, of which the company will contribute 501 million yuan in cash, accounting for 50.1% of the registered capital. Shangzhou Logistics will mainly engage in air cargo transportation and related businesses. The transaction will promote the development of the company’s cross-border e-commerce and other consumer goods supply chain business.
() Receiving supervision letter: urging the company to reply to the inquiry letter and fully reveal the risks related to the semi-annual report in 2021.
On August 30 th, the financial network announced that ST Zhongtian had received the "Supervision Work Letter on Urging ST Zhongtian to Reply to the Inquiry Letter and Fully Reveal the Risks Related to the Semi-annual Report in 2021" from the Supervision Department II of the Listed Companies of Shanghai Stock Exchange. Up to now, the company has not replied to the "Inquiry Letter on the Pledge of Large Creditor’s Rights of Zhongxing Tianheng Energy Technology (Beijing) Co., Ltd." issued by the Shanghai Stock Exchange on June 18th.
The subsidiary of Electric Soul Network plans to purchase a real estate in Xiamen for 81.1939 million yuan.
() Announced that according to the company’s development strategy and business needs, Xiamen Youyou Network Technology Co., Ltd. (hereinafter referred to as "Xiamen Youyou"), a holding subsidiary of the company, plans to purchase the property of the R&D building located in Building 2, plot F11, phase III of Xiamen Software Park, jimei district, Xiamen with its own funds, with a total construction area of 131,384.6 square meters and a total house price of 81,193,900 yuan.
The price of fluorite products of Jinshi Resources has not increased significantly.
() It was announced that the deviation of the closing price of the company’s shares in three consecutive trading days on August 25th, 26th and 27th, 2021 was more than 20%, which was an abnormal fluctuation of stock trading according to the relevant provisions of the Trading Rules of Shanghai Stock Exchange. On August 30, 2021, the company’s stock went up again, and the company’s stock price fluctuated greatly in the short term.
According to the company’s semi-annual report, the average price of acid-grade fluorite fine powder sold by the company from January to June was 2,307 yuan/ton (excluding tax, the same below), down 113 yuan/ton from the same period of last year; The average price of high-grade lump ore is 1,881 yuan/ton, which is 386 yuan/ton lower than the same period of last year. Up to now, the sales price of the company’s fluorite products has not changed greatly and has not increased significantly.
Zhongju High-tech intends to publicly list and sell its subsidiary Zhonghuichuang 89.24% equity.
() Announced that the company intends to publicly list and transfer 89.24% equity of Guangdong Zhonghuichuangchuang Real Estate Co., Ltd. (hereinafter referred to as "Zhonghuichuangchuang") through the property rights exchange, and the listing reserve price is not lower than the appraised value of the underlying assets of 11.169 billion yuan. This transaction is publicly listed, and the transaction object has not yet been determined, which does not constitute a connected transaction for the time being.
According to the announcement, after the completion of this transfer, the company will no longer hold the equity of Zhonghuichuang. Most of the assets of Zhongju’s high-tech real estate business have been divested, and the company’s business will further focus on the main business of healthy food. The funds obtained from this equity transfer will also support the main business of healthy food to a greater extent, which is conducive to the accelerated development of the main business of food.
17,557,500 restricted shares of Fuxin Software will be listed and circulated on September 8th.
Fuxin Software announced that the total number of shareholders of the restricted shares is 354, and the corresponding number of shares is 17,557,500, accounting for 36.47% of the company’s total share capital. The restricted period is 12 months from the date of listing of the company’s shares. The current restricted period is about to expire and will be listed and circulated on September 8, 2021.
149,000 restricted shares of Anjing Food were listed and circulated on September 6th.
() Announcement was issued to release the restricted shares from circulation on September 6, 2021, and the number of shares released this time was 149,000.
China Sinochem started to acquire 57.37% of Fengshen shares.
Our reporter Xiao Yanqing
On the evening of August 30th, () announced that the company had received the Instructions on Launching Relevant Procedures of Joint Reorganization issued by China Sinochem Holdings Co., Ltd. (hereinafter referred to as "China Sinochem") on the same day, and China Sinochem decided to handle the acquisition procedures of listed companies affiliated to China Sinochem Group and China National Chemical Corporation in accordance with relevant regulations from the date when the instructions were issued.
According to the announcement, the purpose of the acquisition is to further deepen the reform of state-owned enterprises, optimize the allocation of resources, and effectively improve China’s innovation ability and industrial position in the global energy, chemical and agricultural fields. With the approval of the State Council, the State Council SASAC agreed to jointly reorganize Sinochem Group and China National Chemical Corporation, and newly established China Sinochem, with the State Council SASAC performing the investor’s duties on behalf of the State Council, and Sinochem Group and China National Chemical Corporation were integrated into China Sinochem Group.
As the State-owned Assets Supervision and Administration Commission of the State Council transferred all the shares of China Sinochem Group and China National Chemical Corporation to China Sinochem for free, China Sinochem indirectly acquired 57.37% of Fengshen’s shares held by the holding company of China National Chemical Corporation.
Fengshen said that after the completion of this acquisition, China Chemical Rubber Co., Ltd. as the controlling shareholder of the company and the State Council SASAC as the actual controller of the company have not changed.
(Editor Tian Dong)
Ping Liu, chairman of Poly Real Estate, and several senior executives increased their holdings by a total of 5,014,900 yuan.
() It is announced that Mr. Ping Liu, the chairman of the company, and 10 senior managers plan to increase their holdings of the company’s shares within six months from August 4, 2021, with a total increase of not less than RMB 8 million and not more than RMB 15 million, and an increase of not more than RMB 14.33 per share.
As of August 30, 2021, the accumulated holding amount exceeded 50% of the lower limit of the planned holding amount interval, and the accumulated holding amount was 5,014,900 yuan.
Tieliu intends to increase the capital of Leishi Technology, a wholly-owned subsidiary, by 58 million yuan.
Tieliu Co., Ltd. announced that the company intends to increase the capital of its wholly-owned subsidiary Leishi Technology (Hangzhou) Co., Ltd. ("Leishi Technology") by 58 million yuan with its own funds, so that Leishi Technology can provide loans to Guangdong Yuntong Sifang Auto Parts Co., Ltd. ("Yuntong Auto Parts") and Fujian Guolian Auto Parts Co., Ltd. ("Guolian Auto Parts"). In order to complete the transaction of acquisition of 100% equity of Yuntong Auto Parts held by Yuntong Sifang Auto Parts Supply Chain Co., Ltd. ("Yuntong Sifang") and 100% equity of Guolian Auto Parts held by Fujian Yuntong Guolian Auto Parts Co., Ltd. ("Yuntong Guolian") and related operating assets.
Huajian Group by-elected Yang Dehong and others as candidates for independent directors.
() Announcement. According to the relevant regulations, the current independent directors of the company, Mr. Zhuo Fumin, Mr. Zhu Jiandi and Mr. Sheng Leiming, have recently submitted to the board of directors of the company their resignation from the relevant positions of independent directors and special committees under the board of directors because they have served for six years. Zhuo Fumin, Zhu Jiandi and Mr. Sheng Leiming will no longer hold any positions in the company after resigning.
The company held the 11th meeting of the 10th Board of Directors on August 30th, 2021, and deliberated and passed the Proposal on By-election of Independent Directors of the Company and Determination of Allowances for Independent Directors, agreeing to by-election Mr. Yang Dehong, Mr. Shao Ruiqing and Ms. Song Xiaoyan as candidates for independent directors of the 10th Board of Directors of the Company. The term of office of by-election of independent directors shall be from the date of deliberation and approval by the shareholders’ meeting to the date of expiration of the term of office of the 10th Board of Directors of the Company. The independent directors of the company expressed their independent opinions on the above proposal.
Sunrise Oriental plans to launch the restricted stock incentive plan in 2021 at a grant price of 2.22 yuan/share.
() Announced that the company plans to launch a restricted stock incentive plan in 2021. The total number of incentive targets granted by this incentive plan is 510, and the grant price is 2.22 yuan/share.
The incentive plan takes the form of restricted stock. The stock source is the RMB A-share common stock of the Company issued by the Company to the incentive object.
The number of restricted shares to be granted to the incentive object in this incentive plan is 24 million shares, accounting for about 3.00% of the company’s total share capital at the time of announcement of this incentive plan. Among them, 23.11 million restricted shares were granted for the first time, accounting for 2.89% of the total share capital of the company at the time of announcement of this draft incentive plan, accounting for 96.29% of the total number of restricted shares to be granted in this plan; The number of reserved restricted shares is 890,000 shares, accounting for 0.11% of the total share capital of the company at the time of announcement of this draft incentive plan, and accounting for 3.71% of the total number of restricted shares to be granted in this plan.
There are no items that should be disclosed but not disclosed in the stock price change of ST Zhongtian.
ST Zhongtian announced that the deviation of the closing price of the company’s shares for three consecutive trading days on August 26th, 27th and 30th, 2021 was more than 15%, which was an abnormal fluctuation of stock trading according to the relevant provisions of the Listing Rules of Shanghai Stock Exchange.
After the company’s self-examination, as of the disclosure date of this announcement, the company confirmed that there are no major matters or important information that should be disclosed but not disclosed.
Zhongju Gaoxin appointed Zou Weidong as Deputy General Manager.
Zhongju High-tech announced that the company held the 28th meeting of the 9th Board of Directors on August 30th, 2021. According to the needs of the company’s operation and management, upon nomination by the general manager of the company and review by the nomination committee of the board of directors, the board of directors agreed to appoint Mr. Zou Weidong as the deputy general manager of the company until the expiration of the current board of directors.
ST Anxin: 4.34 billion yuan was released in the first half of the year.
On the evening of August 30, ST Anxin announced that in the first half of the year, the company continued to promote the resolution of the bottom letter and actively sought to reach a settlement with the holders of the bottom letter of the trust project and other off-balance sheet creditors to resolve related risks. By the end of 2020, it has been found that the total balance of stock letters is 75.276 billion yuan; As of June 30, 2021, the total balance of the stock letter was found to be 70.936 billion yuan, and 4.34 billion yuan had been released during this period.
The five directors of ST Huayu Jiangao intend to reduce their holdings by no more than 160,300 shares.
() Announcement. Recently, the company received the Letter of Notice on Stock Reduction submitted by Mr. Liu Pengju, Director, Mr. Xing Jianjun, Chief Financial Officer, Ms. Sun Yanchun, Secretary of the Board of Directors, Ms. Wang Yanping, Deputy General Manager and Mr. Wang Xiaofei, Supervisor (hereinafter referred to as "five directors, supervisors and senior managers").
Mr. Liu Pengju, the director, intends to reduce his holdings by no more than 43,100 shares, accounting for 0.0078% of the total share capital; Mr. Xing Jianjun, the chief financial officer, intends to reduce his holdings by no more than 29,800 shares, accounting for 0.0054% of the total share capital; Ms. Sun Yanchun, Secretary of the Board of Directors, intends to reduce her holdings by no more than 9,250 shares, accounting for 0.0017% of the total share capital; Ms. Wang Yanping, deputy general manager, intends to reduce her holdings by no more than 74,300 shares, accounting for 0.0134% of the total share capital; Mr. Wang Xiaofei, the supervisor, intends to reduce his holdings by no more than 3,900 shares, accounting for 0.0007% of the total share capital. If the reduction is made through centralized bidding in Shanghai Stock Exchange, the reduction period shall be within 6 months after 15 trading days from the date of disclosure of this announcement, and the reduction price shall be determined according to the market price.
ST Anxin: In the first half of the year, it is necessary to accrue the credit impairment loss of financial assets and the gain from changes in fair value of about 121 million yuan.
On the evening of August 30th, StAnxin announced that, according to preliminary calculation, the company needs to accrue about 121 million yuan of credit impairment loss and fair value change income of financial assets in the first half of 2021, which mainly includes about 102 million yuan of debt investment assets impairment reserve, about 12 million yuan of fair value change income of trading financial assets, about 13 million yuan of impairment loss of receivables and other receivables assets and about 18 million yuan of expected credit loss.
ST Zhongtian: Cheng Shijun resigned as an independent director.
ST Zhongtian issued an announcement, and the board of directors of the company received a written resignation report submitted by Mr. Cheng Shijun /SHIJUN CHENG, an independent director of the company, on August 27, 2021. Mr. Cheng Shijun/Mr. /SHIJUN CHENG applied to resign as an independent director of the company for personal reasons, and will no longer hold any position in the company after his resignation.
The fund shareholding company held by Jinshi Technology is listed in science and technology innovation board.
() Announcement: Chengdu Guoguang Electric Co., Ltd. (hereinafter referred to as "Guoguang Electric"), the shareholding company of Chengdu Tianyi Venture Equity Investment Fund Partnership (Limited Partnership), issued the Announcement of science and technology innovation board Listing of Initial Public Offering on August 30, 2021. Guoguang Electric initially issued 19,354,932 RMB ordinary shares (A shares), of which 15,934,346 shares will be officially listed on the Shanghai Stock Exchange on August 31, 2021. The stock name is "Guoguang Electric" for short and the stock code is "688776".
Huayin Power intends to publicly list and transfer idle real estate.
() Announcement: In order to optimize the company’s asset structure and revitalize the stock of idle properties, the company decided to sell 25 sets of idle properties and 5 idle parking spaces in Rong Feng 2008 Community, No.305, Guanganmenwai Street, Beijing, on the property rights exchange. After completing the disposal of the above-mentioned real estate and parking spaces, it is estimated that the company’s income will increase by about 50 million yuan.
As of June 30, 2021, the net book value of the assets to be transferred totaled 6.31 million yuan, the appraised value of the assets totaled 126 million yuan (including tax), and the appraised value added was 120 million yuan.
(): The proposed acquisition of Conch New Energy Company, which is mainly engaged in photovoltaic power generation, is conducive to building a new industrial growth level.
On August 30th, CONCH announced that on August 30th, 2021, the company signed an equity transfer agreement with Conch Investment Company, stipulating that the company would acquire 100% equity of Conch New Energy Company, with a total consideration of RMB 443,210,600. After the completion of the acquisition, Conch New Energy Company will become a wholly-owned subsidiary of the company.
According to the announcement, Conch New Energy Company is a limited liability company incorporated in China in March 2018, with a registered capital of RMB 500 million on the date of announcement. Its main business scope includes: photovoltaic power generation, wind power generation, technology development and technical services in the field of energy storage system, construction, operation and management of power projects, power sales, power engineering and electromechanical engineering construction.
The company’s decision to acquire Conch New Energy Company is mainly based on the following reasons and the expected benefits from the transaction: (1) Conch New Energy Company mainly engages in photovoltaic power generation and other businesses, which can provide power support for the cement production of the Group and play a good auxiliary supporting role in the development of the main cement industry of the Group; (2) While focusing on the development of the main cement industry, the Group will give full play to its capital advantages and location advantages to develop new energy business, which will help to create a new industrial growth level and promote the diversified development of the company’s industry; (3) New energy has good environmental protection benefits. By using clean energy, carbon dioxide emissions in the cement production process can be effectively reduced, which is in line with the current national peak carbon dioxide emissions and carbon neutrality policies and is conducive to promoting the transformation and upgrading of the Group and even the cement industry. Therefore, the company believes that the acquisition is beneficial to the company’s high quality and sustainable development.
The recent average cost of CONCH is 37.40 yuan, and the stock price runs below the cost. In the short market, and there is an accelerated downward trend. In the past five days, the funds of this stock have generally been in an outflow state. According to statistics, in the past 10 days, the main force has concentrated a certain amount of chips, showing a moderate control state. The company is operating well, and most institutions believe that the long-term investment value of the stock is high.
Tianbang shares intend to sell aquatic feed business to Tongwei shares with a total transaction amount of 1.08 billion yuan.
() announced that the company intends to sell aquatic feed business to (). The company intends to transfer 100% equity of Ningbo Tianbang Feed Technology Co., Ltd. (hereinafter referred to as "Ningbo Tianbang"), Qingdao Qihao Biotechnology Co., Ltd. (hereinafter referred to as "Qihao Bio"), Ningbo Tianbang Biotechnology Co., Ltd. (hereinafter referred to as "Ningbo Bio") and Vietnam Tianbang Feed Co., Ltd. (hereinafter referred to as "Vietnam Tianbang") to Tongwei. After the completion of this transaction, the aquatic feed business of listed companies will be completely divested, which will not affect the normal operation of other businesses of listed companies.
The sale of aquatic feed business is one of the contents of the strategic cooperation between the company and Tongwei Co., Ltd., aiming at forming industrial synergy with complementary advantages with Tongwei Co., Ltd. through the form of strategic cooperation, creating greater commercial value and economic benefits for both parties, jointly promoting the healthy and sustained coordinated development of the industry and jointly creating a good industrial development order. After the sale of aquatic feed business, the company will focus on pig breeding and supporting animal-derived food industry chain, and strengthen pig breeding, fattening technology and process control. This transaction is expected to generate a pre-tax asset disposal income of 420 million yuan, which is included in the company’s current profit and loss in 2021.
The controlling shareholder of Fuda Alloy intends to reduce its shareholding by no more than 3.44%.
Fuda Alloy announced that Wang Dawu, the controlling shareholder of the company, intends to reduce the holding of no more than 4,128,600 shares of the company through centralized bidding and/or block trading, accounting for 3% of the company’s total share capital; Wang Dawu’s unanimous pedestrians Qian Chaobin and Li Fengfei plan to reduce their holdings by no more than 428,680 shares and 176,400 shares by centralized bidding from September 23 to December 31, 2021, with the reduction ratio not exceeding 0.31% and 0.13% of the company’s total share capital respectively.
Zhijiang biological controller plans to increase its holdings by 10 million yuan to 15 million yuan.
Zhijiang Bio announced that Shao Junbin, the actual controller and chairman of the company, based on his confidence in the company’s future development and recognition of the company’s long-term investment value, plans to increase his shareholding in the company through centralized bidding transactions within six months from September 1, 2021. The total amount of shares to be increased this time is not less than 10 million yuan and not more than 15 million yuan.
Jingneng Real Estate plans to acquire 100% equity of Lifu Real Estate for 361 million yuan.
On August 30th, () Co., Ltd. announced that it intends to acquire the equity of Beijing Lifu Real Estate Development Co., Ltd..
According to the new media of Viewpoint Real Estate, Jingneng Real Estate Co., Ltd. plans to acquire 100% equity of Beijing Lifu Real Estate Development Co., Ltd. held by Beijing Jintai Real Estate Development Co., Ltd. through the agreement of Beijing Equity Exchange for 361 million yuan. It is reported that Jintai Real Estate is a wholly-owned enterprise under Beijing Energy Group Co., Ltd., the controlling shareholder of the company, and is a related legal person of the company.
It is understood that before the related party transaction, there were 9 undisclosed related party transactions between Jingneng Real Estate and Jingneng Group, totaling 10.4649 million yuan, which did not reach 0.5% of the absolute value of the company’s latest audited net assets, and it did not conduct similar equity transfer or related transactions with Jingneng Group and Jintai Real Estate; After the related party transaction is completed, Jingneng Real Estate will hold 100% equity of Lifu Company, and Lifu Company does not provide external guarantee or entrust financial management. It is reported that this related party transaction is conducive to solving the company’s horizontal competition problem, expanding the business scope of the company’s affordable housing field, expanding the company’s business scale and enhancing the company’s profitability.
According to the data, Jintai Real Estate was established on December 2, 1998, which is a wholly state-owned enterprise. The legal representative of the company is Zhao Equation, with a registered capital of 1.56 billion yuan, and its main business is real estate project development and property management. By the end of 2020, the audited total assets of Jintai Real Estate were 15.898 billion yuan and the net assets were 928 million yuan. In 2020, Jintai Real Estate had an operating income of 3.363 billion yuan, a total profit of 50 million yuan and a net profit of-53 million yuan.
Lifu Company was established on April 21st, 2004. It is a wholly-owned subsidiary of Jintai Real Estate with a registered capital of 200 million yuan. It is a real estate company whose core business is the development and construction of affordable housing. The shareholding structure of the company is 100% wholly owned by Jintai Real Estate.
After 545 days, Kweichow Moutai changed coaches again.
On August 30th, Kweichow Moutai Co., Ltd. (hereinafter referred to as "Kweichow Moutai") announced that it had received the document recommending the chairman candidate, saying that according to the relevant documents of Guizhou Provincial People’s Government, Ding Xiongjun was recommended as the director and chairman candidate of Kweichow Moutai, and it was suggested that Gao Weidong no longer serve as the chairman and director of the company. Regarding the authenticity of this news, beijing business today reporter interviewed the relevant departments of Kweichow Moutai and learned that the news of coaching change is true, but whether the work is handed over at present is unknown, and the details are unknown.
Xiao Zhuqing, an expert in consumer goods marketing in China, said that Ding Xiongjun is a doctor-type senior talent, who has comprehensive management experience and rich experience and qualifications in economic management. Kweichow Moutai needs an aggressive "head" in the process of great changes in liquor industry.

Maotai changes coaches again.
Beijing business today reporter learned through the website of Guizhou Provincial People’s Government that the provincial government issued a notice on the dismissal of Gao Weidong and others, saying that Gao Weidong was decided to be the director of Guizhou Coal Geology Bureau, and Ding Xiongjun was no longer the director of Guizhou Energy Bureau.
According to public information, Ding Xiongjun was born in Chongyang, Hubei Province, in August 1974, with a postgraduate degree and a doctor of science. He joined the work in July 1995 and joined the Communist Party of China (CPC) in June 1994. He is currently a member of the Party Committee, secretary, director and chairman of Kweichow Moutai Distillery (Group) Co., Ltd. in China. Although Ding Xiongjun is a chemical professional, he once served as the executive vice mayor of Bijie City as a platform for the local liquor industry.
It is worth noting that Kweichow Moutai changed coaches this time, only 545 days apart from the last time. Some insiders believe that Gao Weidong’s sudden departure may be related to the slowdown of Kweichow Moutai’s performance growth. In the first half of this year, Kweichow Moutai achieved revenue of 49.087 billion yuan, up 11.68% year-on-year, and net profit of 24.654 billion yuan, up 9.08% year-on-year. The latest half-year net profit growth of Kweichow Moutai is less than 10%, which can be traced back to 2015.
According to Xiao Zhuqing’s analysis, Kweichow Moutai needs an aggressive "head" in the process of great changes in the liquor industry. Ding Xiongjun is a doctoral senior talent with comprehensive management experience. At the same time, there is also a wealth of experience and qualifications in economic management.
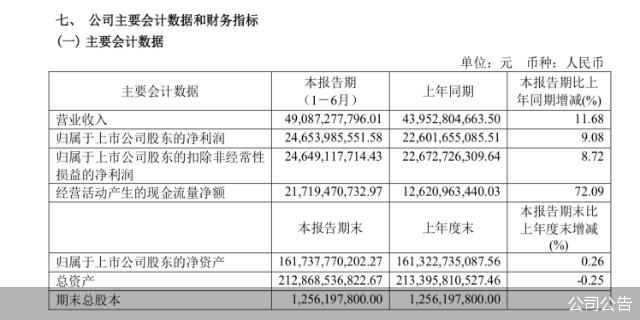
Slow performance growth
Since taking office in March last year, Gao Weidong has made many attempts to stabilize prices in the terminal market. It not only requires dealers to sell wine 100% out of the box, but also increases the expansion of direct sales channels. Gao Weidong said at the end of last year that Kweichow Moutai will continue to deepen the reform of the marketing system, accelerate the construction of self-operated, supermarket-operated and e-commerce channels, and form a good situation of complementary and coordinated development with social channels and self-operated systems.
Beijing business today reporter learned that during Gao Weidong’s tenure, Kweichow Moutai vigorously developed direct sales channels. According to the semi-annual report of Kweichow Moutai in 2021, in the first half of this year, the direct sales channel of Kweichow Moutai achieved revenue of 9.504 billion yuan, an increase of 84.44% compared with 5.153 billion yuan in the same period last year. The wholesale agency channel achieved revenue of 39.505 billion yuan.
Xiao Zhuqing believes that in the Gao Weidong era, direct sales channels were actively expanded, and Maotai was supplied to Internet platform customers and new retail business chain customers at a price of 1,499 yuan/bottle, which not only increased the sales profit of Maotai, but also directly faced consumers and understood more consumer needs.
In order to stabilize the price of liquor, Kweichow Moutai not only increased direct sales channels, but also asked Maotai dealers to sell liquor 100% out of the box this year. At the same time, Kweichow Moutai will conduct random checks on dealers from time to time, and will recycle the boxes to prevent the specialty stores from violating the rules and regulations. However, from the effect point of view, the terminal sales price of Feitian Maotai has not been effectively controlled. At present, the terminal market price remains at around 2,900 yuan/bottle. Although compared with the previous terminal sales price of 3,000 yuan/bottle, with the coming of traditional festivals such as Mid-Autumn Festival and National Day, the demand for high-end liquor will gradually increase, further increasing the terminal sales price.
While the price stabilization policy has had little effect, the growth rate of Kweichow Moutai’s performance has also slowed down in recent years. beijing business today learned from the recent performance of Kweichow Moutai that in 2018-2020, Kweichow Moutai achieved revenue of 73.639 billion yuan, 85.43 billion yuan and 94.915 billion yuan respectively, with year-on-year growth of 26.49%, 16.01% and 11.1% respectively. The net profit was 35.204 billion yuan, 41.206 billion yuan and 46.697 billion yuan respectively, with year-on-year growth of 30%, 17.05% and 13.33% respectively. It is not difficult to find from the data that since 2019, the growth rate of Kweichow Moutai has slowed down significantly.
Liu Liqing, chief consultant of Beijing Shangbing Cutting Brand Organization, said that the main reasons for the change of coaching in Kweichow Moutai were poor price control, slow growth rate and the collapse of the capital market. Behind this is the ability of comprehensive management of Kweichow Moutai, which involves many problems such as historical legacy and complicated interests.
The market value evaporated by 1 trillion yuan.
While the growth rate of performance is slowing down, the market value of Kweichow Moutai is also evaporating. As of today’s close, Kweichow Moutai closed at 1586 yuan/share, with a daily decline of 0.63%. In fact, since Kweichow Moutai entered August, the total market value has continued to decline. The peak of total market value was 2.2 trillion yuan on August 10th, when the share price of Kweichow Moutai was 1,799 yuan/share.
Industry analysts believe that with the gradual withdrawal of capital, it is also expected that Kweichow Moutai will have insufficient growth potential. Previously, the share price of Kweichow Moutai rose sharply, mainly due to the lack of high-quality targets in the capital market. After the Spring Festival this year, the main funds gradually withdrew from the liquor sector, which is also one of the reasons for the unsatisfactory overall performance of the liquor sector this year.
Beijing business today reporter noted that since June this year, Kweichow Moutai capital market has shown a downward trend. Since the opening of the first transaction in June this year, the total market value of Kweichow Moutai has dropped from 2.81 trillion yuan to 1.99 trillion yuan, and the market value has evaporated by 0.82 trillion yuan. As a leading liquor enterprise, Kweichow Moutai’s highlight moment in the capital market dates back to the beginning of this year. In February this year, the total market value of Kweichow Moutai successfully exceeded 3 trillion yuan, and its share price also hit record highs, once exceeding the 2600 yuan/share mark in intraday trading.
From 3.3 trillion yuan to 1.99 trillion yuan, the market value of Kweichow Moutai evaporated by 1.3 trillion yuan in seven months. Liu Liqing said that Kweichow Moutai is an enterprise with a long history in the East. Therefore, whether it is the performance of enterprises or the performance of the capital market, there should be no ups and downs. However, the recent downward adjustment of Kweichow Moutai capital market is unacceptable to shareholders and investors.
Beijing business today reporter Zhao Review Zhai Fengrui
The final winning rate of online distribution of Shanghai Yizhong is 0.02597%.
According to the announcement of the exchange, Shanghai Yizhong announced the online subscription situation and the winning rate. The number of effective subscription households in this online offering is 6,182,514, and the number of effective subscription shares is 29,327,054,000. After the callback mechanism was launched, the final number of shares issued offline was 17,774,500, accounting for 70.00% of the number issued after deducting the number of strategic placements; The final number of shares issued online was 7,617,500, accounting for 30.00% of the number issued after deducting the number of strategic placements. After the callback mechanism was started, the final winning rate of online issuance was 0.02597431%.